You can easily block USB drives on all Intune-managed devices by using different methods available on the Intune admin center. Blocking USB drive access is a must for every organization as it can save the organization from data leaks.
In Today’s world, users use BYOD devices or a device provided by your company. In either case, if users are accessing any confidential information from the device which can be saved and then copied to your external storage then it could be a security breach event.
To prevent this security breach, the use of removable storage must be blocked on all corporate devices. However, In some cases, there would be certain users/specific devices that will require USB drive access. We will exclude those devices from this policy as an exception to allow for USB access.
We will explore different options to configure the policy and then perform testing on a test device to confirm if it’s working fine.
Blocking the use of Removable storage can be done using any of below methods:
- Intune admin center -> Endpoint Security -> Attack Surface Reduction Policy
- By creating a Device Configuration Profile from the Intune admin center.
- Using Intune Device Remediations
Table of Contents
Method 1 – Attack Surface Reduction Policy
Let’s check the steps to block USB drive access by creating an Attack Surface Reduction (ASR) policy.
- Sign in to Intune admin center.
- Click on Endpoint security > Attack surface reduction.
- Click on + Create Policy
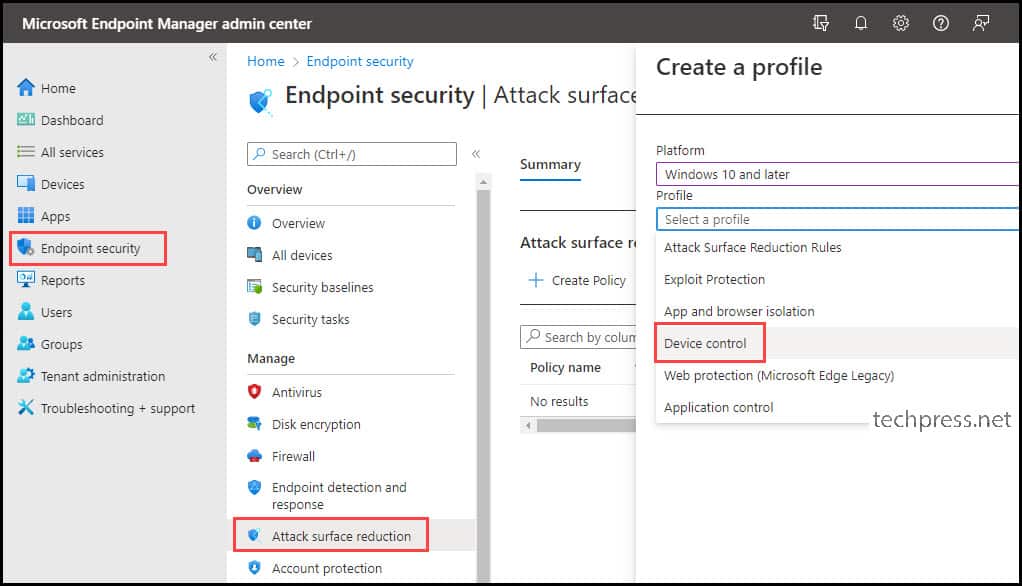
Basics Tab
Provide a Name and Description of the Policy and Click on Next.
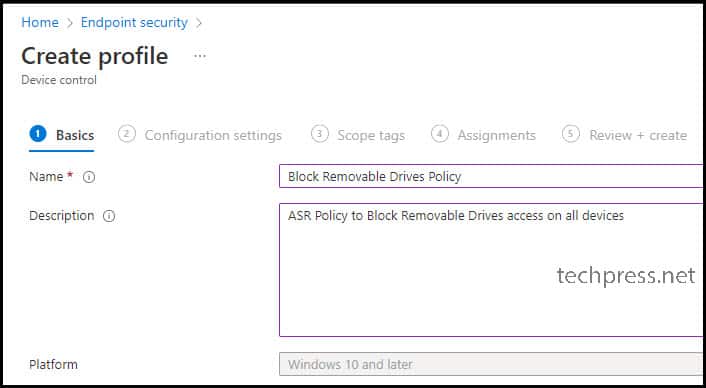
Configuration settings Tab
Scroll down to find a setting named “Removable Disk Deny Write Access” under Storage. Use the drop-down and select Disabled. Click on Next.
Scope tags
Click on Next.
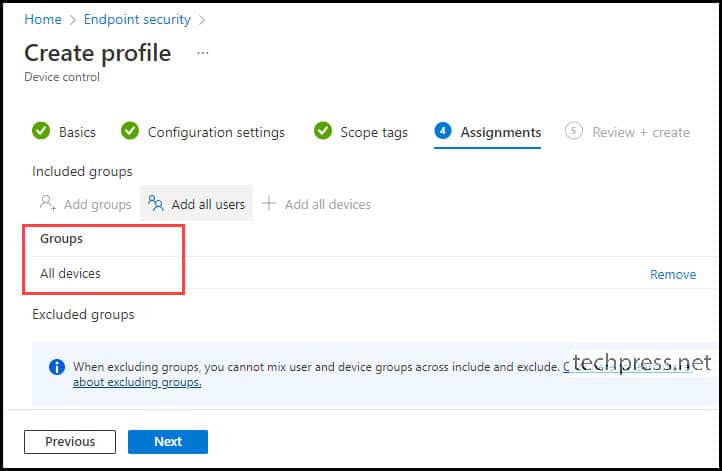
Assignments
Assign this profile to an Entra security group containing users or devices. If you add users to the group, then the profile will get applied even if a user changes their device. But if you want to apply this profile to specific devices only then target this profile to an Entra security group containing devices only.
Method 2 – Create a Device Configuration Profile
- Sign in to the Intune admin center
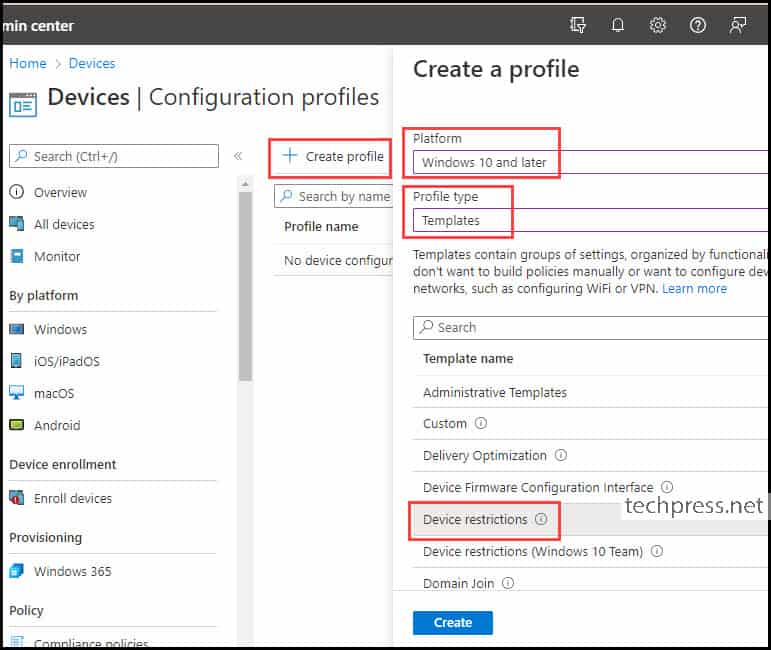
- Go to Devices > Configuration profiles
- Click on Create > New Policy
- Platform: Windows 10 and later
- Profile type: Templates
- Template name: Device restrictions
- Basics Tab – Provide a Name and Description.
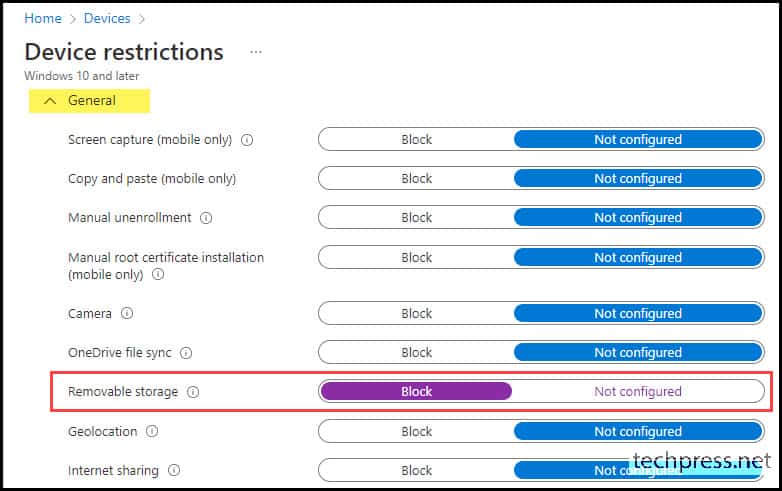
- Configuration settings – Under General Category, locate the Removable storage setting. Use the toggle switch to set it to Block.
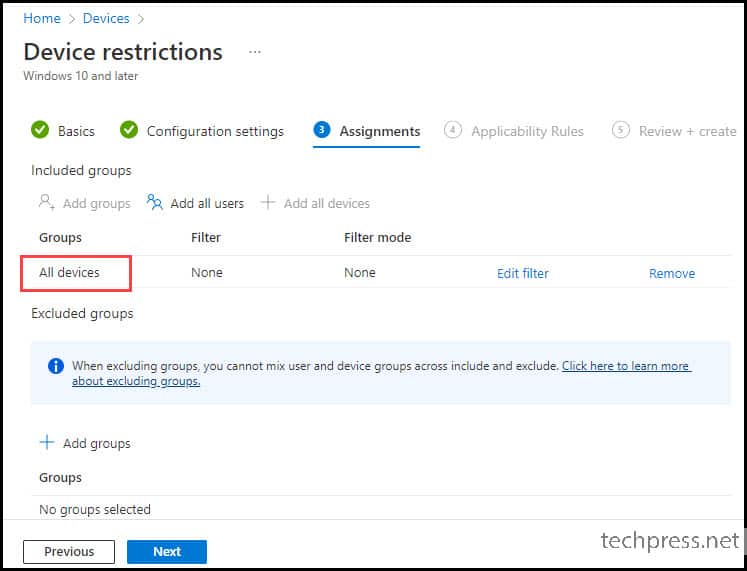
- Assignments – Assign this policy to either an Entra security group or All devices.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync either from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Another way to trigger the Intune device check-in process is by restarting the device.
End-user Experience
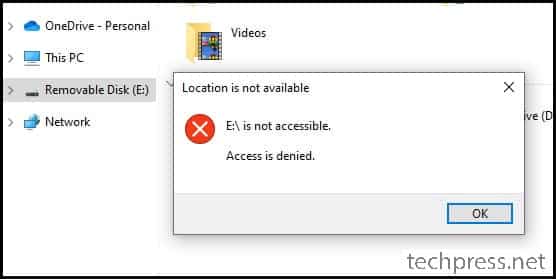
Once this policy has been successfully applied to target devices, Users will not be able to access USB drives and will get an error: Location is not available, E:\ is not accessible. Access is Denied.
USB Drive Block Policy Exclusions – Option 1
Whether you use an ASR Policy or a Device Configuration Profile, it will block USB drive access on all Intune Managed devices. However, you have the option to create an Entra security group, add devices to this group, and then exclude the group from this policy.
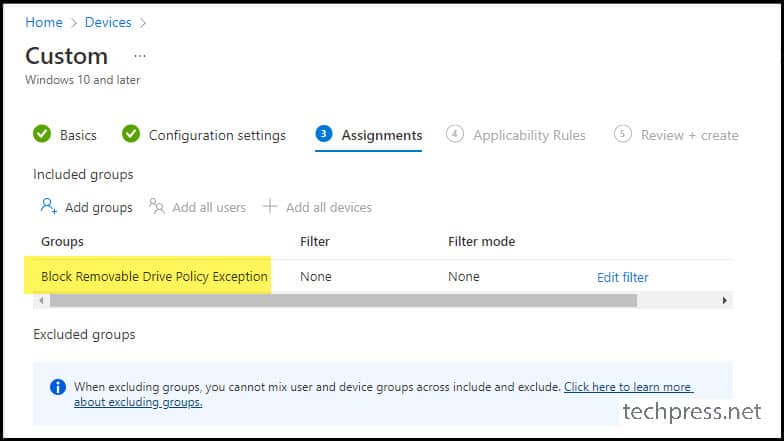
I’ve created an Entra security Group named “Block Removable Drive Policy Exception” and added devices to this group for exclusion from the policy. All devices added to the “Block Removable Drive Policy Exception” group will retain access to USB drives.
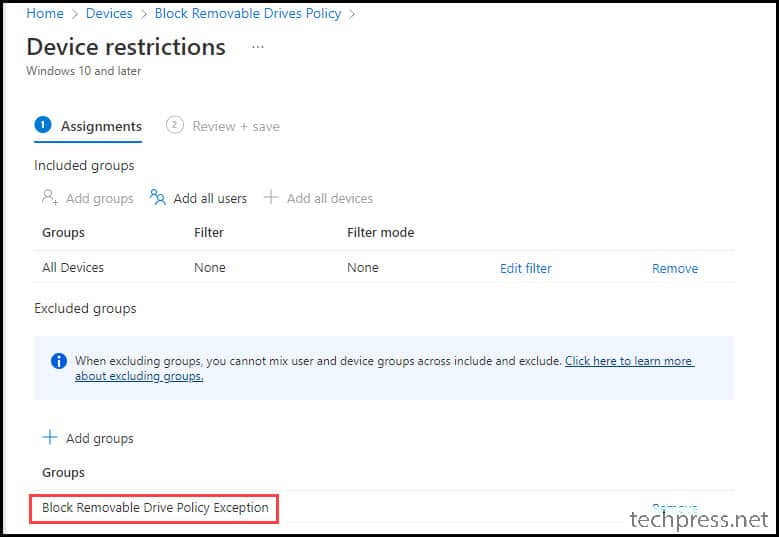
The screenshot below illustrates a device that was included in the “Block Removable Drive Policy Exception” Entra security group, allowing it to access the USB drive.
USB Drive Block Policy Exclusions – Option 2
As demonstrated in the “USB Drive Block Policy Exclusions – Option 1“, we’ve established an Entra Security group named “Block Removable Drive Policy Exception” and added it to the Excluded group section of the “Block Removable Drives Policy”.
This setup ensures that devices added to the “Block Removable Drive Policy Exception” group will have USB drive access.
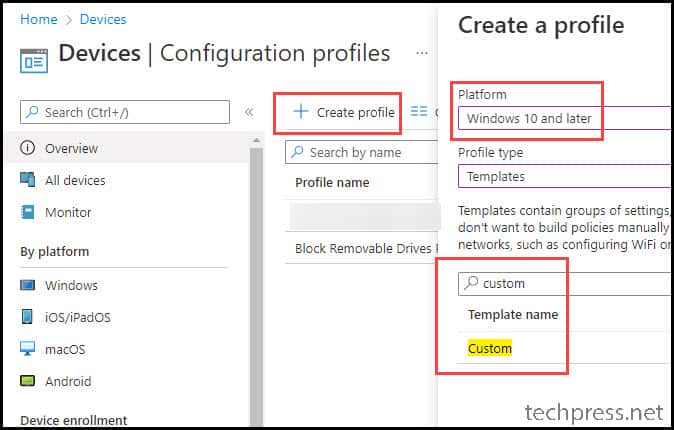
There is another way you can allow specific devices to have access to the USB drive by using a Custom OMA-URI Setting. Let’s see how to create a policy and use this option.
- On the Intune admin center, Go to Devices > Configuration Profiles > Create > New Policy.
- Platform: Windows 10 and later
- Profile Type: Templates
- Template Name: Custom
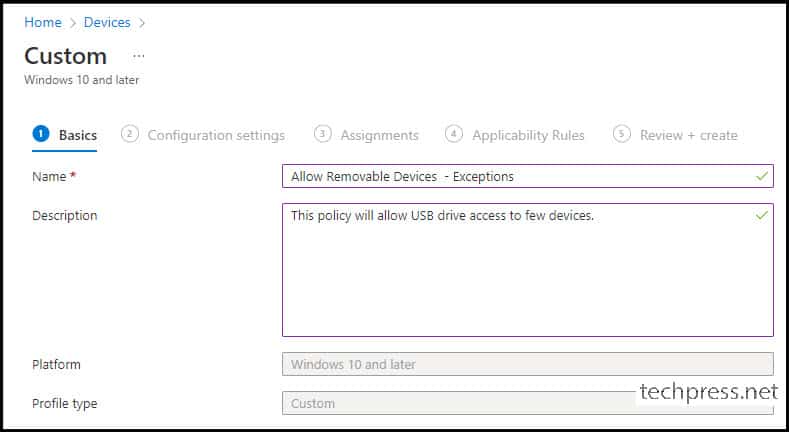
- Basics Tab – Provide a Name and Description of the profile. For Example: Allow Removable Devices – Exceptions.
- Configuration Settings – Click on Add button to add OMA-URL settings.
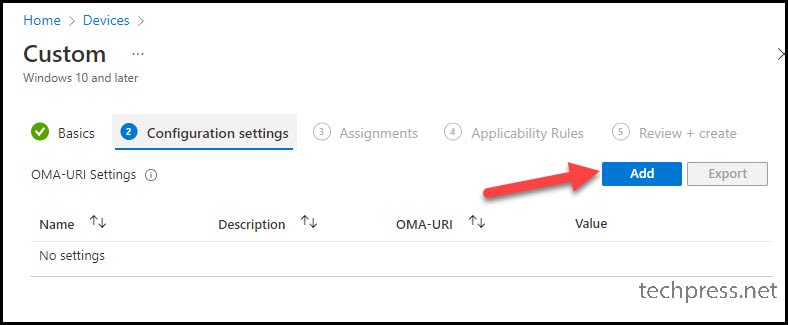
- Provide below OMA-URI Settings:
- Name: Windows 10 – Allow USB Drive
- Description: Allow USB Drive OMA URL Setting
- OMA-URI: ./Device/Vendor/MSFT/Policy/Config/System/AllowStorageCard
- Data type: Integer
- Value: 1
- Assignments tab – Assign this policy to an Entra security group which contains devices on which you do want to “Allow” USB drive access.
Method 3 – Using Intune Device Remediations
You can leverage Intune Device Remediations to block USB drives. For a detailed, step-by-step guide, please refer to the link: Block USB Drives access on Windows using Intune remediations.

I’m looking for the correct way to implement the following:
* Block all removable storage devices except specific list of allowed USB removable drives
I looked at the ASR devicecontrol thing but I’m struggling with wildcards for the class (tried to do “block USBSTOR\*”) but that does not seem to work (error 65000)
What does work is enter “RemovableMediaDevices” in the “primary ID” field, that blocks the devices, however, I cannot override it then with a specific USB removable drive Hardware ID.
Any thoughts ?
Hi Vincent,
You can use “Allow installation of devices that match any of these Device IDs” policy in Intune to allow certain devices while still keeping the USB port blocked for all other devices. Please refer to below blog post for this. Let me know if it helps. https://learn.microsoft.com/en-us/mem/intune/configuration/administrative-templates-restrict-usb