This blog post will provide the steps on how to disable TLS 1.0 and TLS 1.1 on Windows servers. TLS protocol is used to ensure privacy and data integrity when two applications communicate. SSL and TLS are both cryptographic protocols, as SSL does not provide a sufficient level of security compared to TLS, SSL 2.0 and SSL 3.0 have been discontinued. TLS 1.0 was released in 1999, TLS 1.1 in 2006, TLS 1.2 in 2008, and TLS 1.3 in 2018.
If you’d like to learn more about these protocols, understand their differences, and explore security enhancements, you can visit the Protocol RFCs (Request for Comments) at the following links: TLS 1.0 RFC, TLS 1.1 RFC, TLS 1.2 RFC, and TLS 1.3 RFC.
There are two ways to disable TLS 1.0 and TLS 1.1 on Windows Servers. Let’s explore both of these options.
Contents
Option 1: Disable TLS 1.0 and TLS 1.1 using GPO
- Log in to a domain controller as a domain administrator.
- Press Windows + R to open the Run dialog box.
- Type
gpmc.mscand press Enter to open the Group Policy Management Console. - Expand the Group Policy Objects folder, right-click on it, and select New.
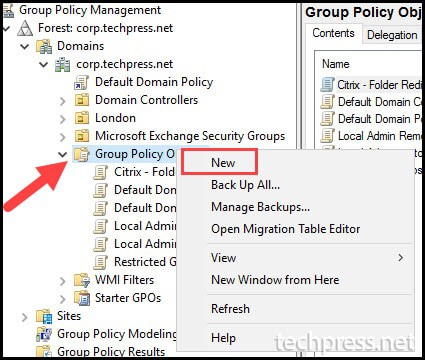
- Provide a Name of the GPO. For Example: Disable TLS 1.0 and TLS 1.1 Windows servers.
- Right-click on the GPO and click Edit.
- Navigate to Computer Configuration > Preferences > Windows Settings > Registry.
- Right-click on Registry > Choose New > Select Registry Item.
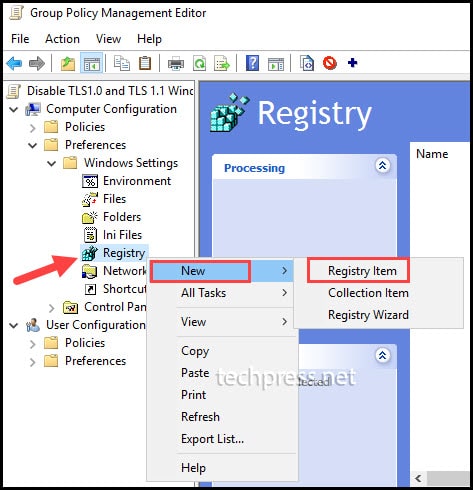
- Create a registry Item.
In the next step, we will create registry keys and entries to disable TLS 1.0 and TLS 1.1. It is also recommended to disable SSL 2.0 and SSL 3.0. Most newer Windows operating systems have TLS 1.2 enabled by default. However, if you want to manage TLS 1.2 and TLS 1.3 protocols, you can use the provided registry keys corresponding to those versions.
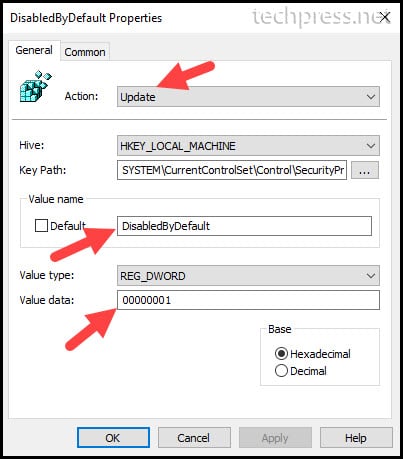
- Action: Choose Update from the drop-down menu. Selecting Update will create the registry keys and entries if they are not already found on the target devices.
- Hive: Select HKEY_LOCAL_MACHINE
- Key Path: You can either browse to the registry path or provide the path directly.
- Value Name: We will be creating two registry entries per protocol. DisabledbyDefault and Enabled.
- Value type: Select REG_DWORD.
- Value type: 1 means the setting is Enabled and 0 means the setting is Disabled.
- Repeat the process to create registry keys for each protocol. Here are the registry keys you can create for each protocol.
Registry Keys to disable TLS 1.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server] "Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server] "DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client] "Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client] "DisabledByDefault"=dword:00000001Registry Keys to disable TLS 1.1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server] "Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server] "DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client] "Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client] "DisabledByDefault"=dword:00000001Registry Keys to disable SSL 2.0 [Recommended]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server] "Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server] "DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client] "Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client] "DisabledByDefault"=dword:00000001Registry Keys to disable SSL 3.0 [Recommended]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server] "Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server] "DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client] "Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client] "DisabledByDefault"=dword:00000001Registry Keys to Enable TLS 1.2 [Recommended]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] "Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] "DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] "Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] "DisabledByDefault"=dword:00000000Registry Keys to Enable TLS 1.3 [Optional]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server] "Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server] "DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client] "Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client] "DisabledByDefault"=dword:00000000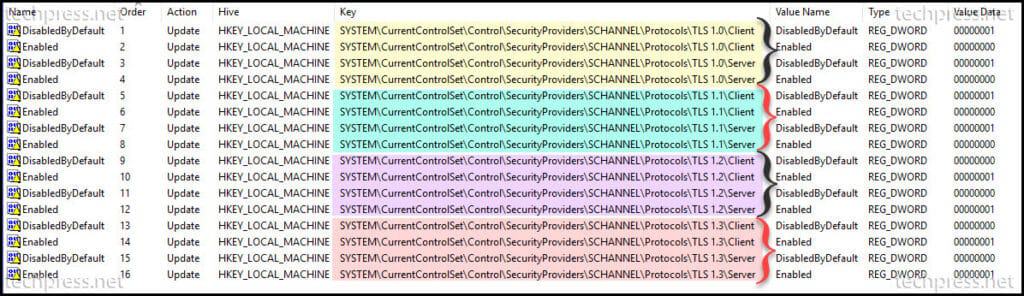
- Link the GPO to Server OU.
- Please note that a restart of the server is required to complete the configuration changes.
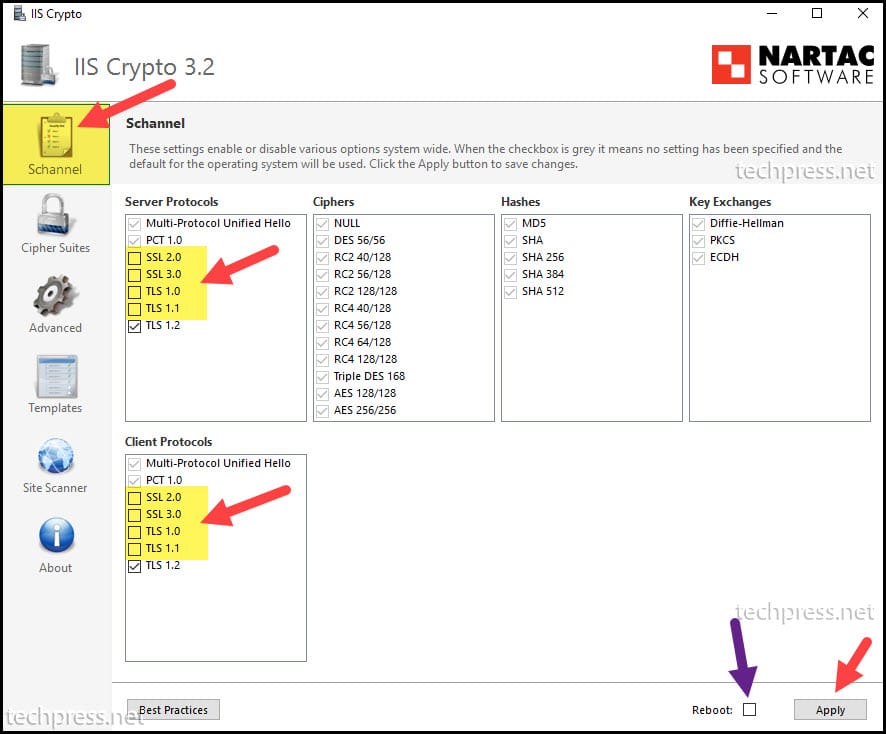
Option 2: Disable TLS 1.0 and TLS 1.1 using the IIS Crypto Tool
If your Windows servers are not domain-joined, or you prefer not to create a GPO to disable deprecated SSL and TLS protocols, an alternative option is to download and install the IIS Crypto tool on the Windows server. With this tool, you can manually select the checkboxes to disable or enable SSL/TLS protocols.
- Log in to Windows Server using administrator credentials.
- Download the IIS Crypto GUI tool.
- Launch the IIS Crypto tool as an administrator.
- Uncheck SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1 from Server Protocols.
- Uncheck SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1 from Client Protocols.
- Reboot the server.
- Repeat Steps 1 to 6 on each server where you want to disable deprecated SSL and TLS protocols.

Great Article!!