This post will show you how to find Microsoft Graph PowerShell scopes. You can install Microsoft Graph PowerShell module and connect to it using Connect-MgGraph cmdlet. A -scopes parameter with required permissions must be provided when establishing a connection with graph. For example, User.Read.All or Group.Read.All. These scopes determine the level of access you get to perform a specific task via Graph.
Before connecting to Graph PowerShell, it’s important to identify the least-privilege scopes required for your task. Once you know them, you can connect using: Connect-MgGraph -Scopes <string[]>. There are several ways to figure out which scopes (permissions) you need. Let’s go through the different options.
Contents
1. Using Microsoft Graph Explorer
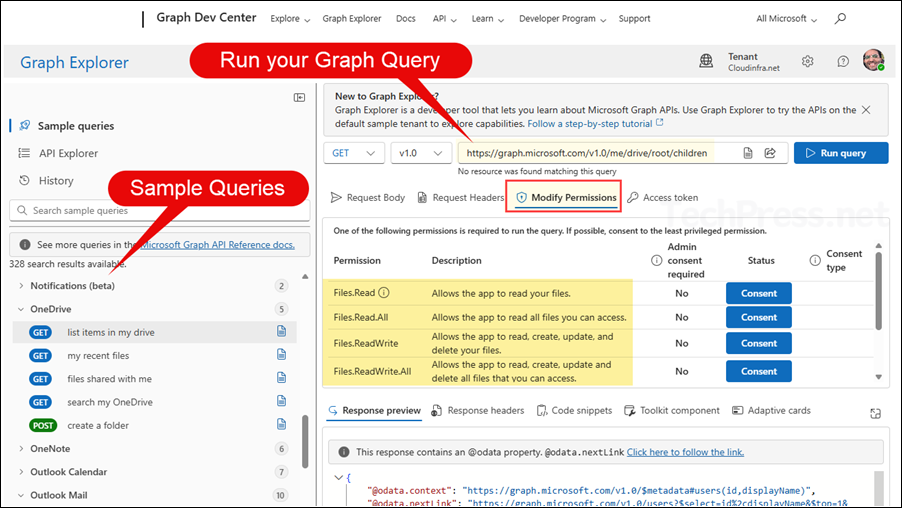
To determine which permissions are needed for a specific task, run your query in Graph Explorer and then click Modify permissions. It will show the permissions required to execute the query. Whenever possible, choose and consent to the least-privileged permission. You don’t need to use all the listed permissions, use the least permissive permission and then step-up if needed.
2. Using Find-MgGraphCommand
You can also use the Find-MgGraphCommand cmdlet. Its output includes the permissions required to run the specified cmdlet, helping you identify the required scopes for the graph command. Below example uses Get-MgUser cmdlet, you can replace that with the cmdlet you are using.
Find the Graph operation behind a cmdlet (Get-Mguser) and its required permissions
(Find-MgGraphCommand -Command Get-MgUser -ApiVersion v1.0).Permissions | Select-Object Name, PermissionType, DescriptionRun this command to get full info
(Find-MgGraphCommand -Command Get-MgUser -ApiVersion v1.0).Permissions | fl *3. Using Find-MgGraphPermission
The following commands use the Find-MgGraphPermission cmdlet to search for a string and return a list of all matching permissions that can be used with the -Scope parameter.
Searching user.read string
Find-MgGraphPermission -SearchString "user.read" -PermissionType Delegated | Select-Object Name, ConsentSearching DeviceManagement string
Find-MgGraphPermission -SearchString "DeviceManagement" -PermissionType Application | Select-Object Name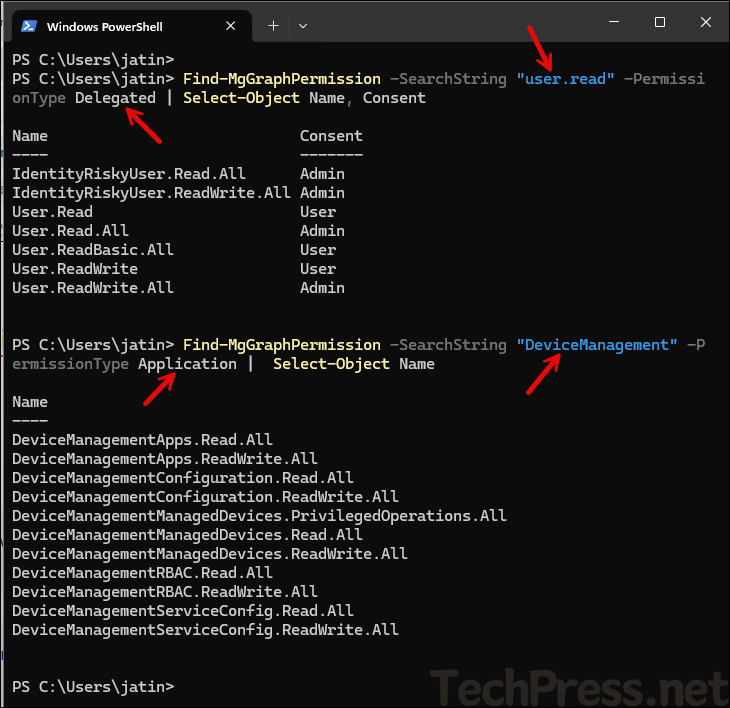
4. Check Microsoft Documentation
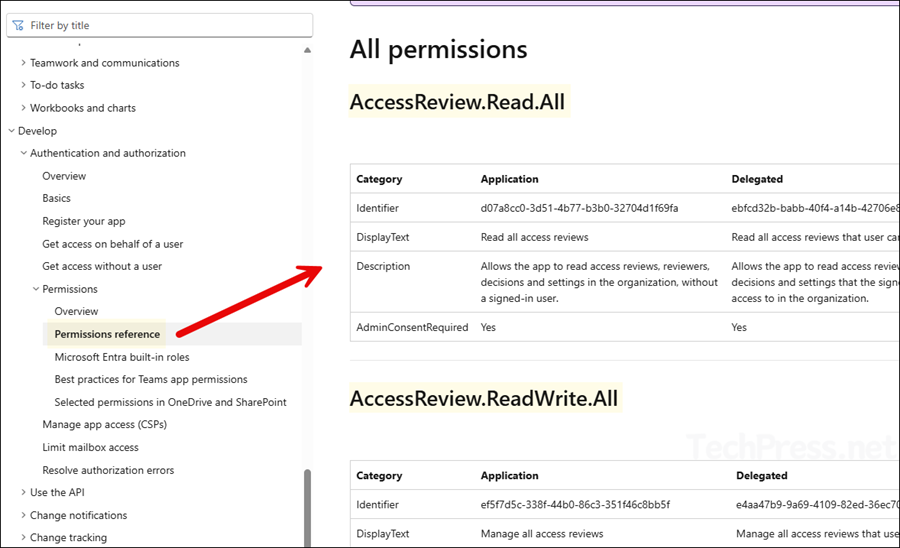
Refer to Microsoft’s documentation permissions reference page which includes all the permissions with their identifier, display name, description, consent requirements, and type (Delegated or Application). Use Ctrl+F to find the permission you require, then review its description to confirm if it fits your scenario.
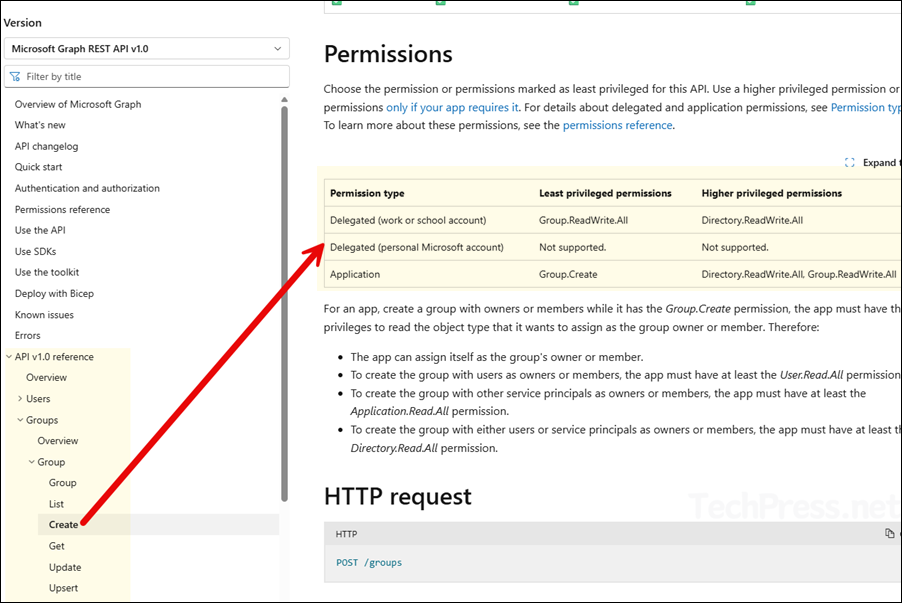
Another helpful resource is the Microsoft Graph REST API reference. It lists all the objects on the left-hand side, expand it and click on an action like List or Create, the required permissions are shown on the right-hand side under the Permissions section.
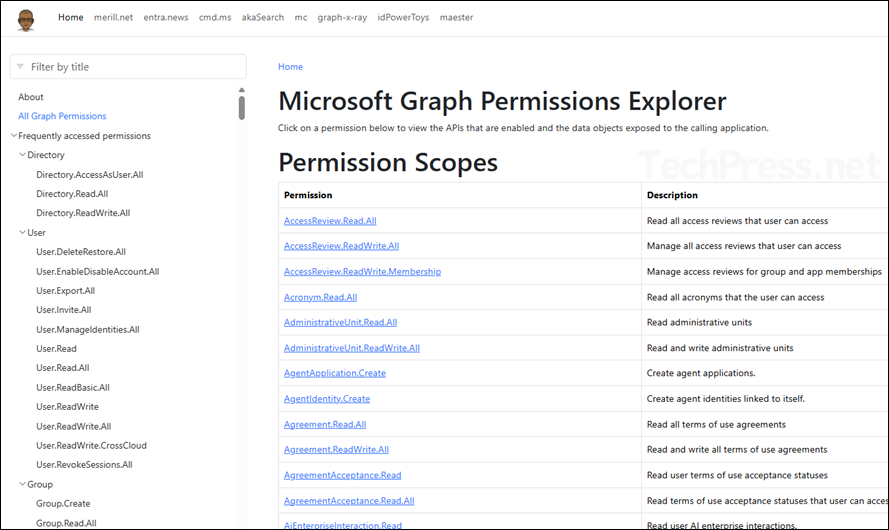
5. Using Community Graph Permission Explorer
This is a third-party website https://graphpermissions.merill.net/permission/ which looks like a Microsoft website. You can use that as a reference to check the permission level required.
6. Check your Consented Permissions
Another option, though it is more reactive than proactive, is to check the scopes after you’ve connected to graph. Running the Get-MgContext command shows the permissions you’ve already consented to. If you find the list too permissive, you can adjust your scopes as needed.
Check your consented scopes
Connect-MgGraph -Scopes "User.Read.All","Group.Read.All" -NoWelcome
Get-MgContext | Select-Object -ExpandProperty Scopes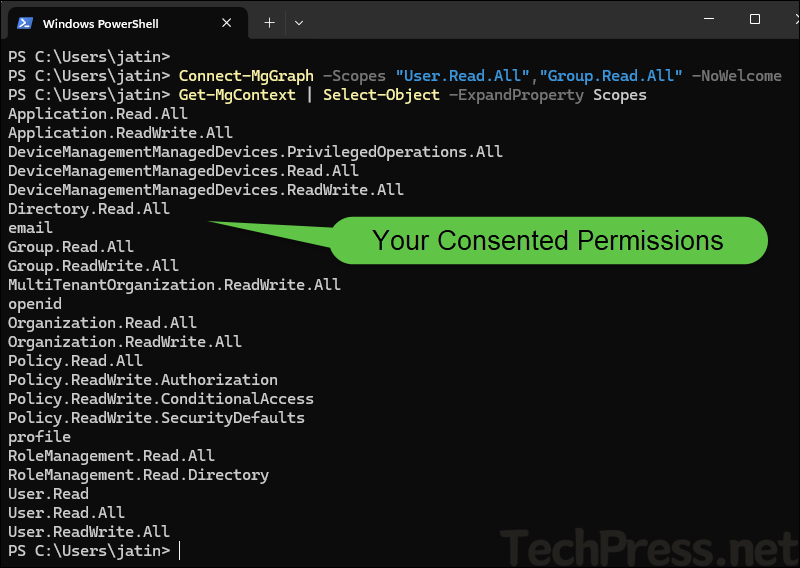
Wrapping Up With Few Tips
- Delegated vs. Application: Use delegated scopes for interactive admin scripts; use application permissions for unattended jobs (requires admin consent).
- Least privilege: Start with read-only scopes (e.g.,
Directory.Read.All) and step up only when a cmdlet demands more. Graph Explorer’s Modify permissions panel is your fastest check.
- Version matters: Required scopes can differ between v1.0 and beta, always query with the same API version you’ll use.
