In this blog post, I’ll demonstrate the steps to setup Multi Admin Approval (MAA) in Intune. MAA adds a second pair of eyes for high impact actions, reducing mistakes and limiting the damage from unapproved changes. It can also help in providing additional security to protect an administrator account which may have been compromised.
To setup MAA, you create an access policy to protect a group of resources and configuration changes. In the access policy, you select the policy type which defines the type of resource to protect, like Apps, Script, or role etc. Once the policy is in place, any changes to the protected configuration will require an approval from a second administrator (member of an approvers group).
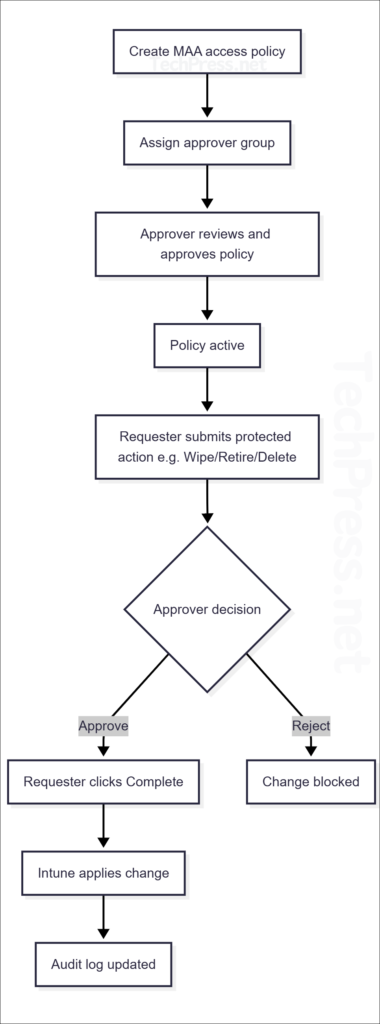
1) Requester submits the change with a business justification –> 2) a different admin approves or rejects the request –> 3) If approved, requester clicks Complete request –> 4) Intune implements/applies the changes.
Multi admin approval (MAA) workflow
As of now, you can create Access policies to protect below resources in Intune:
- Apps: This includes create, edit, assign, and delete actions.
- Device delete, retire, wipe action: Approval will be required to delete, retire or wipe a single device or bulk devices in admin portal or Graph APIs.
- Role: Any changes to the role area, like using a built-in role or creating a custom role, will require approval. Also, for edit, assignment and delete operations.
- Script: A script policy will require approval for scripts, such as PowerShell scripts or remediation scripts. Actions like create, edit, assign, and delete will require approval.
Contents
Prerequisites
- At least two admins account in the tenant.
- To create MAA policies: Intune Service Administrator or a custom role with Approval for Multi Admin Approval permission.
- Approvers must be in the approver group that the policy uses, and that group must be part of at least one Intune role assignment.
- An Intune license must be assigned to the administrator for approving the request.
Multi Admin Approval (MAA) Workflow
- Create an Access policy under MAA to protect any supported resource (Creating an access policy requires approval from another administrator).
- Admin will create or edit a protected item and provides a business justification.
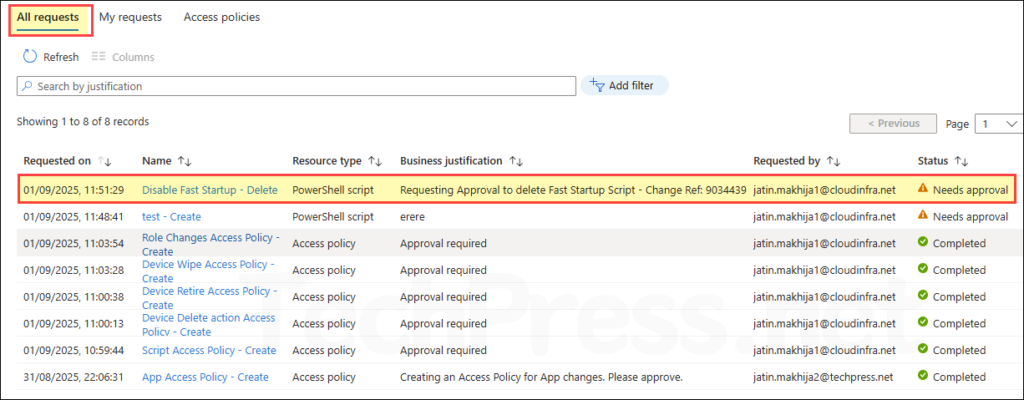
- Another admin (part of approvers group) will go to Tenant administration > Multi Admin Approval > All requests and can approve or reject the request.
- If the request is approved, requestor will go to Tenant administration > Multi Admin Approval and can click All requests or My requests tab to complete the request. Intune will then process the request. If a request is not actioned by an administrator, it will expire after 30 days.
Below diagram shows Multi admin approval (MAA) workflow.
Create Multi admin approval (MAA) Access Policy
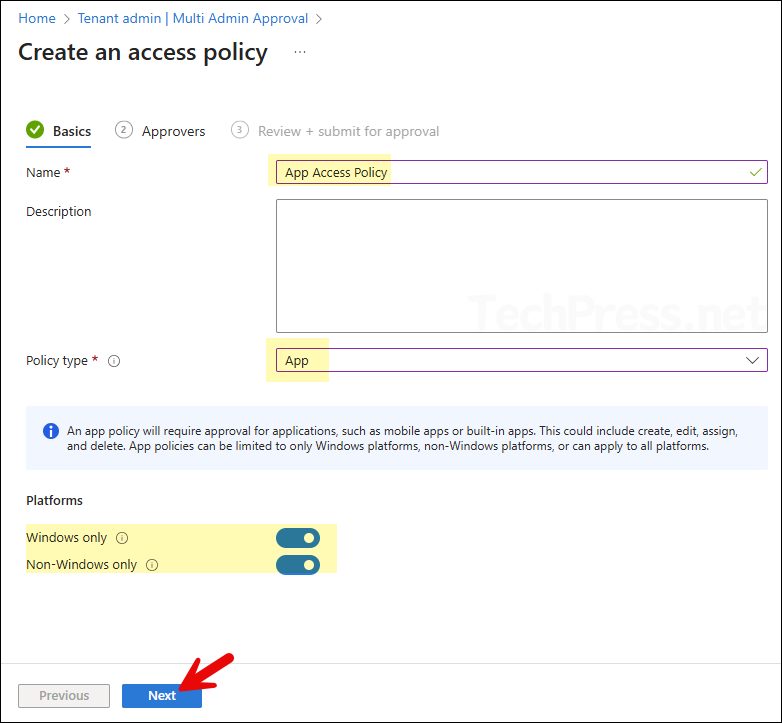
Create an access policy using below steps. For demonstration purposes, I will create a policy to protect app changes (create, edit, assign, and delete). Therefore, I will select App as the policy type.
- Sign in to the Intune admin center > Tenant administration > Multi Admin Approval > Access policies > Create.
- Basics tab: Provide a Name and Description of the policy.
- Policy type: Select a resource to protect (For example: App).
- Platforms: There are below two options to select from:
- Windows only: Protects the selected resource on Windows 10 and later, Windows 8.1 and later, and Windows10X.
- Non-Windows only: Protects the selected resource on Android Device Administrator, Android Enterprise, iOS, iPadOS, and macOS.
Please note that Device actions, scripts, role policy type applies to all platforms, therefore you will find below options enabled greyed out for these options.
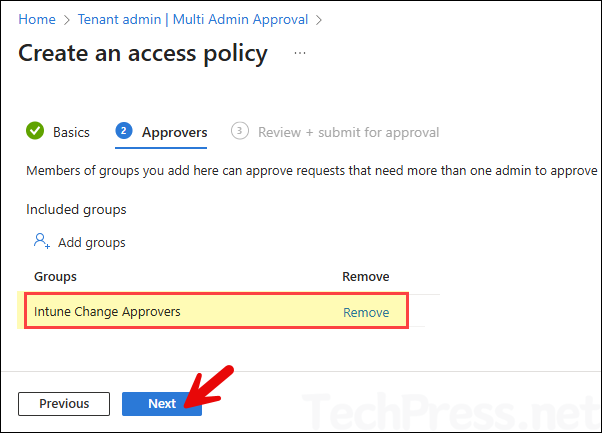
- Click Add groups, then select your approver group. Any member of the approver group can approve or reject requests. I created a group called Intune Change Approvers in Entra ID and added it under the Approvers tab.
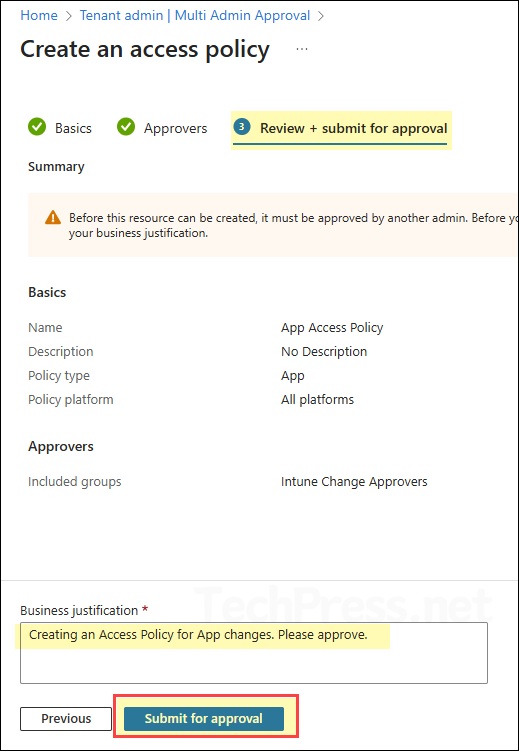
- Creating an access policy requires approval from another administrator. Provide a business justification, then click Submit for approval.
Approve Access Policy Request
Sign in with a different admin account, then go to Tenant administration > Multi-admin approval > All requests. Review the business justification provided by the administrator. Status will show as Needs approval, click the request.
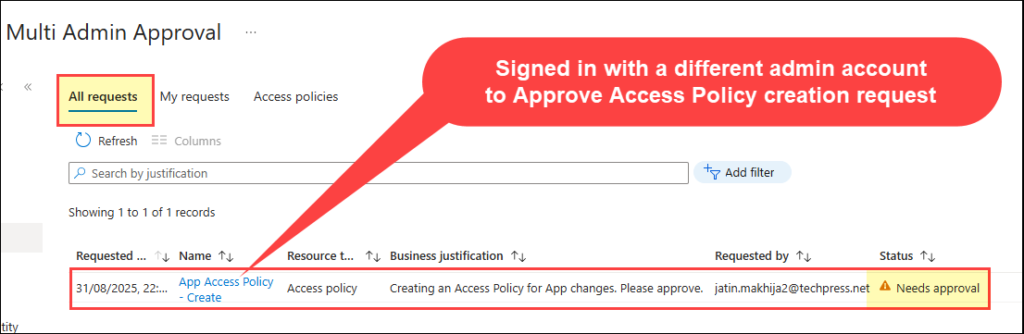
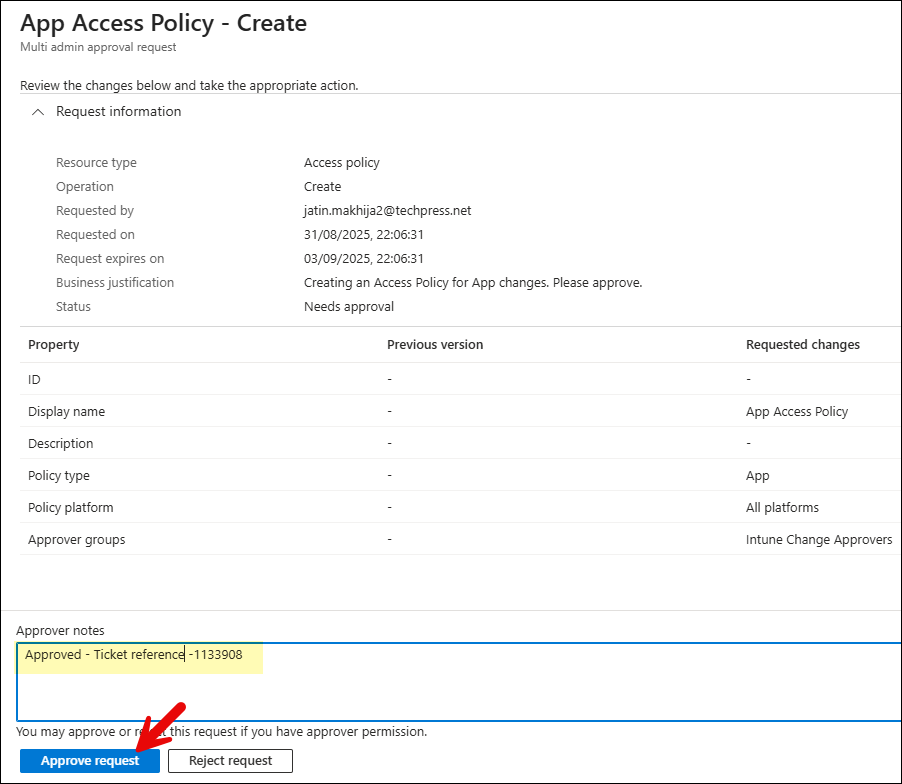
- Click the request and add your approver notes. You can either Approve or Reject the request. The requester will be notified accordingly.
Complete Approval Request
Before any changes can be implemented, the requester must complete the request and confirm the changes. If the requester no longer wishes to implement the policy, they can click Cancel request.
- In the Intune admin center, go to Tenant administration > Multi-admin approval > All requests. Select the request, then click Complete request.
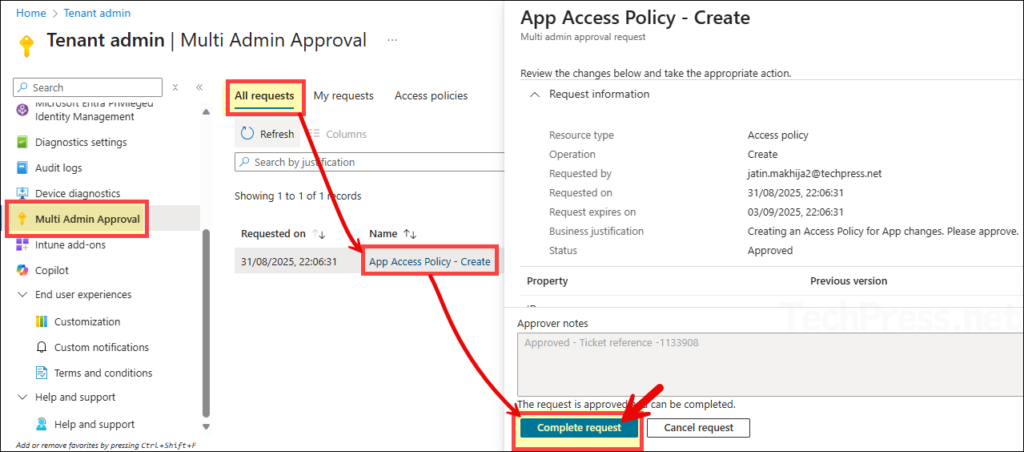
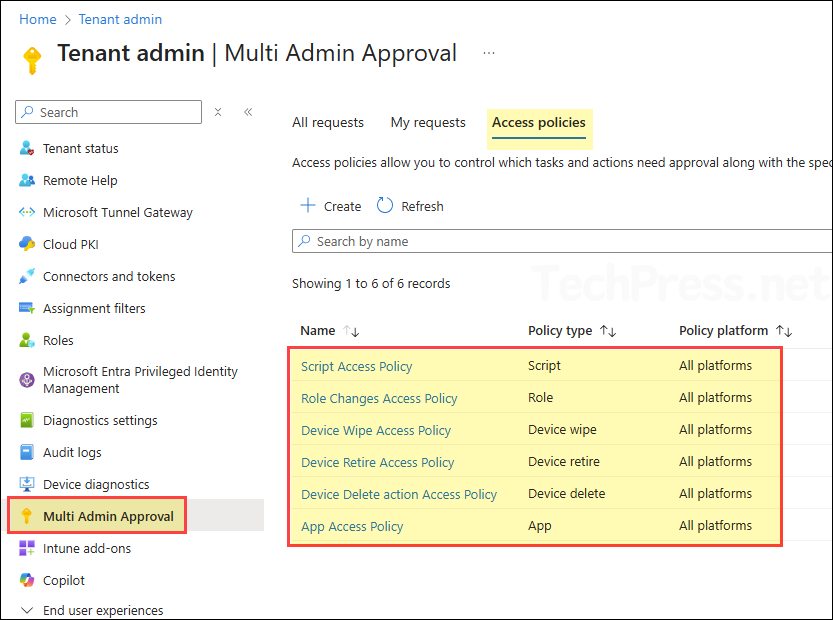
- Now verify that the access policy appears under the Access policies tab.
Add More Access Policies
- Repeat these steps to create access policies for scripts, device actions, and role changes. Provide a business justification and submit each for approval. Below screenshot shows the view from an approver screen where the requests to create policies are pending approval.
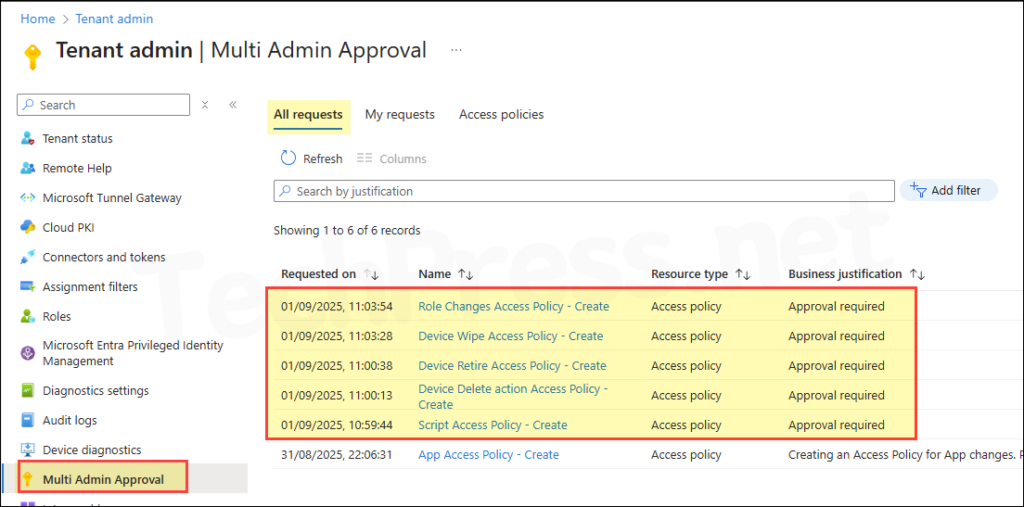
- All requests have now been approved.
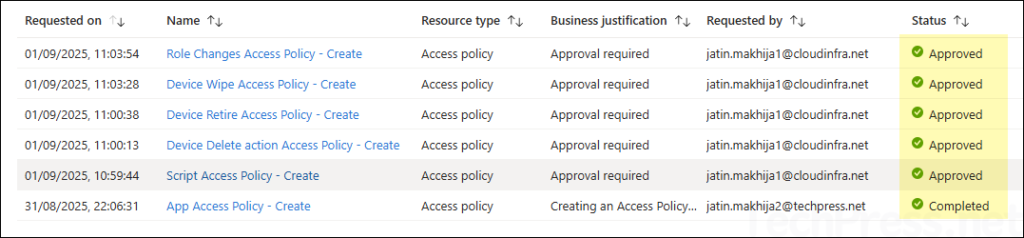
- Once all requests have been approved, the requester must go to Tenant administration > Multi-admin approval > All requests, select each request, and click Complete request.
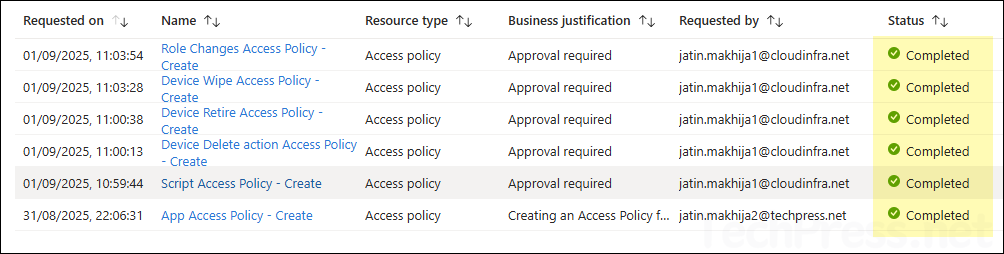
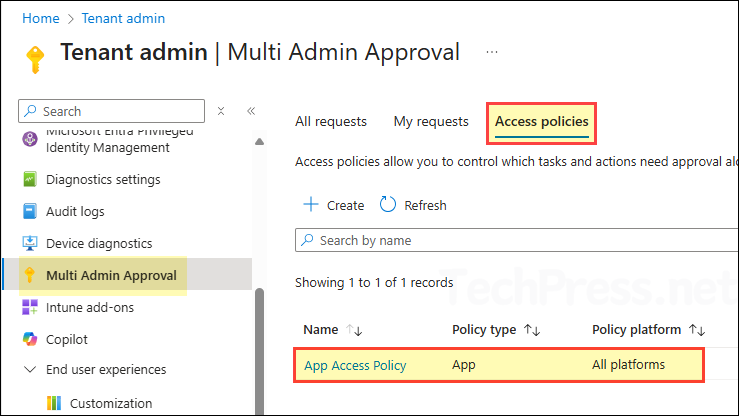
- Once the requests are completed, all requested access policies will be created and appear under the Access policies tab.
End User/Administrator Experience
Now that we’ve set up access policies to protect all resources supported by the multi-admin approval feature, administrators will not be able to change protected policies without approval from a member of the approvers group (in our case, the Intune Change Approvers group). Let’s see the admin experience for one of the protected policy. The experience of requesting and approving the changes for other policies will be the same.
- Sign in to the Intune admin center > Devices > Scripts and remediations > Perform any action on scripts and remediation section. Let’s try to delete one of the script.
- Clicking on Delete button requires business justification. Provide a business justification and click Submit for approval.
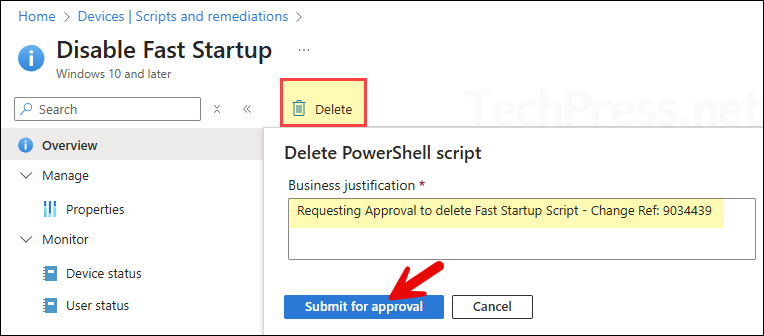
- Sign in as Approver, then go to Tenant administration > Multi-admin approval > All requests. Review the business justification provided by the administrator. If the status will show as Needs approval, click the request.
- Enter Approver notes, then choose Approve or Reject. For this example, we will go with Approve request.
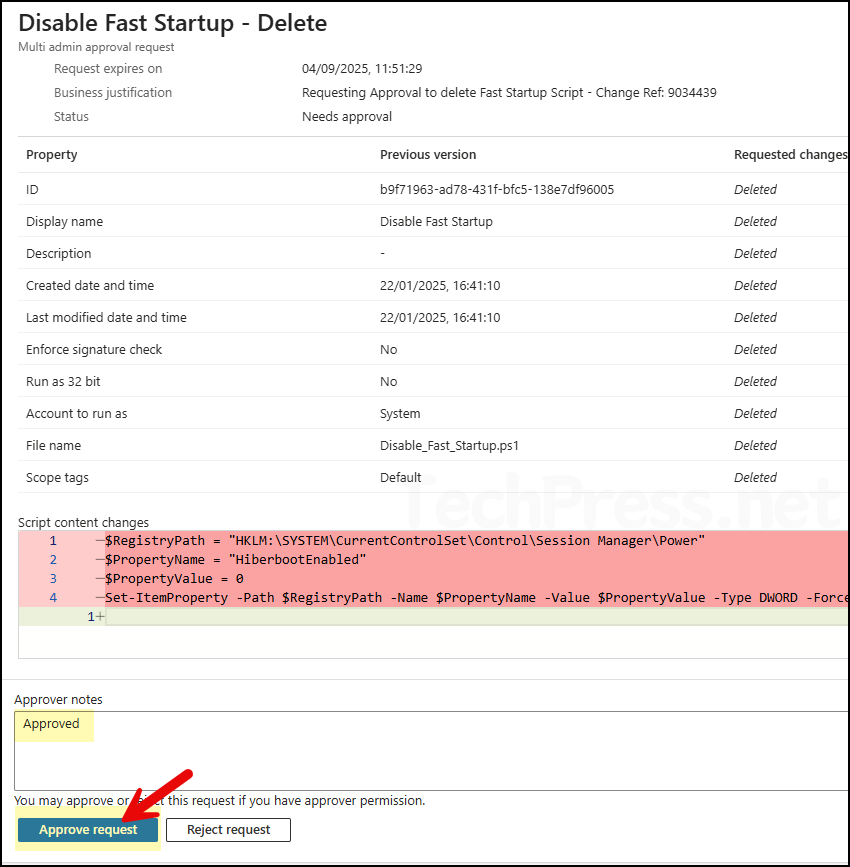
- Once the request is approved, the requested action for script deletion will be implemented by Intune and the script will be deleted.
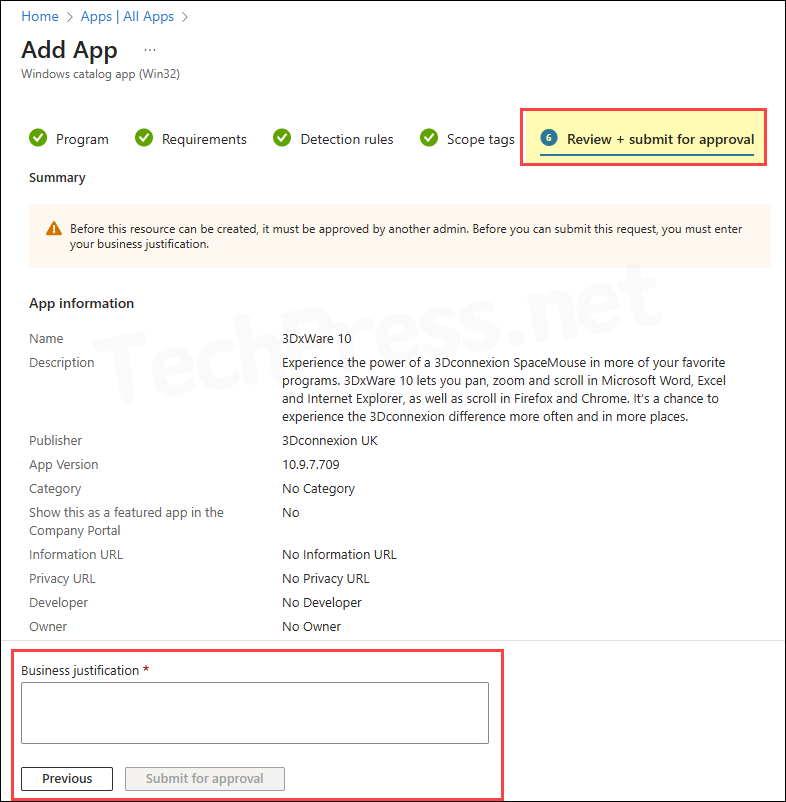
- Now take another example and try making a change to any other protected resource. When adding an app, the final step that used to be Review + create is now Review + submit for approval. Provide a business justification and select Submit for approval.
Troubleshooting
You may encounter issues during the setup or approval phase of Multi Admin Approval. To start with that, here is one error I got while approving a request. The administrator who tried the approval had an Intune license and was a Global Administrator. However, the approval still failed with the following error:
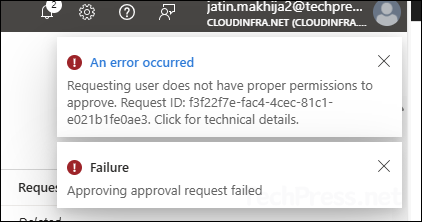
Requesting user does not have proper permissions to approve
{"error":{"code":"BadRequest","message":"{\r\n \"_version\": 3,\r\n \"Message\": \"Requesting user does not have proper permissions to approve - Operation ID (for customer support): 00000000-0000-0000-0000-000000000000 - Activity ID: f3f22f7e-fac4-4cec-81c1-e021b1fe0ae3 - Url: https://fef.msub06.manage.microsoft.com/StatelessRoleAdministrationFEService/deviceManagement/operationApprovalRequests('84a288a5-c6c6-4a46-8d55-8c1fd282d68a')/microsoft.management.services.api.approve?api-version=5025-04-10\",\r\n \"CustomApiErrorPhrase\": \"\",\r\n \"RetryAfter\": null,\r\n \"ErrorSourceService\": \"\",\r\n \"HttpHeaders\": \"{}\"\r\n}","innerError":{"date":"2025-09-01T10:56:58","request-id":"d20cf318-09b3-4b26-8000-84d2d9604e64","client-request-id":"f3f22f7e-fac4-4cec-81c1-e021b1fe0ae3"}}}
It turned out to be a very basic setup issue, the administrator who was approving the request was not a part of the approvers group. Once I added the user to the approver group, I could approve the request. Please note, after adding the admin in the approver group, you may have to wait for couple of minutes for group membership propagation.
A general checklist to prevent Issues with respect to Multi Admin Approval:
- Scope tags (if used) match the approver’s role scope.
- Approver is in the policy’s Approvers group.
- Approver group is included in at least one Intune role assignment (If required, add the group to Read Only Operator to provide the least privilege).
- Approver is different from the requester.
- Access policy is Approved and Completed.
Notifications
Intune does not email or alert approvers. For urgent changes, ping approvers to ask for approval over Teams or Slack or any other communication medium. If an approval is already pending for a change, a new request cannot be submitted for the same object. Cancel the request and resubmit it.
Conclusion
In this post, we set up and configured Multi Admin Approval (MAA) in Intune. We walked through the MAA workflow, demonstrated the implementation steps, showed how to submit a request and get it approved, and finished with troubleshooting tips. I hope this helped you understand and implement this Intune feature. For more information and reading on Multi admin approval in Intune, refer to Microsoft docs: Use multiple administrative approvals in Intune.
