How to Use Scope Tags in Intune: Step-by-Step with RBAC: In this blog post, I will show you how to create and use Scope tags in Intune. Scope tags are labels you attach to Intune objects (apps, policies, profiles, scripts, etc.) and to devices so that admins only see and manage what’s tagged for them. Roles define what an admin can do; scope tags determine which objects they can see, alongside Scope (groups) that limit which users/devices they can affect.
Contents
Key Benefits of using Scope tag
- You can delegate administration of Intune tasks based on region, department, team etc.
- It works on least privilege model. For example, A London office admin cannot see or view Paris profiles.
- Clean view of the Portal, Admins only see the relevant objects, which reduces the chances to make mistakes.
- You can use Scope tags with Dynamic Entra ID groups, which makes them even more powerful and make the segregation automatic.
Important Points about Scope Tags
- Default scope tag: Intune automatically adds a built-in Default scope tag to untagged objects that support tags.
- Auto-apply to devices via groups: When creating a scope tag, you can assign it to device groups, so devices in those groups automatically get that tag (auto assignments can overwrite manual tags; multiple assignments accumulate).
- Object creation inheritance: When an admin creates an object, the scope tags from their role assignment are applied automatically. For example, if the Help Desk Operator role is assigned to the London Help Desk group with the London scope tag, any member of that group who creates an Intune profile or policy will have the London tag applied automatically.
- Bypass tags: Intune administrators and Global administrators can see everything on the Intune portal.
- Maximum limit: You can assign a maximum of 100 scope tags to a role.
Planning Stage
Creating scope tags and assigning it to a role is super easy and won’t take much time. It’s the planning and documentation stage which can take most of your time, especially if there are multiple teams with different RBAC requirements. Below are some of the planning tips you can use.
- Create a list of different departments, regions, Environment (production, dev, test) and their access requirements.
- What level of access is required? Which objects they want to see on Intune portal? Etc.
- Create a naming convention for scope tags. For example: London, Paris, Tag-Prod, Tag-Dev etc.
- Create or use existing device dynamic groups. Prepare a list of device dynamic groups for each region, it can speed the creation and assignemnt of scope tags. For example: London Devices, Paris Devices, New York Devices etc.
- Identify admin groups (Members): Who needs access?, Scope (groups): On which objects they can act on and Scope (tags): what they can see?
Example Scenario: Regional Delegation with Intune Scope tags
Let’s use an example scenario to understand how scope tags can be used and implemented. The below diagram shows the scope tag structure for two branch offices in London and Paris, managed by separate admins. Our goal is to give each admin team permission only over its own devices and visibility only to objects relevant to its region.
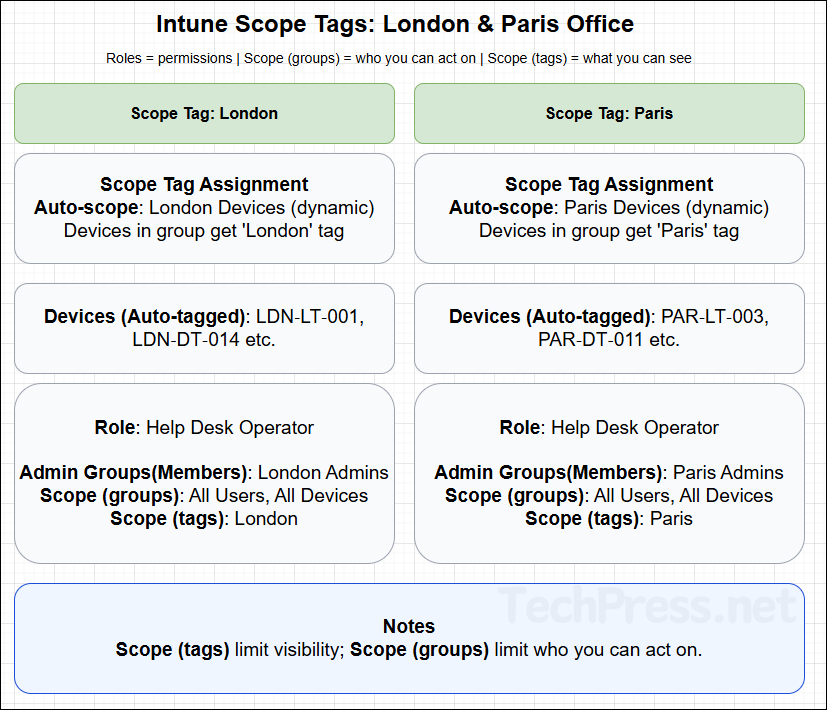
1) Create and Assign Scope Tags
As per our example scenario, we will create two scope tags, London and Paris. Go to Intune admin center > Tenant administration > Roles > Scope tags > click + Create. Assign it to your respective office devices. Assign London office tag to London devices (dynamic group) and Paris Office tag to Paris devices (dynamic group).
This will ensure that the scope tags are auto assigned to the devices in each region based on dynamic group membership. All London devices will get London tag and Paris devices will get Paris tag.
| Scope tag | Assigned to device group (auto-scope) |
|---|---|
| London | London Devices |
| Paris | Paris Devices |
Auto-scope keeps device tags up to date as devices move in or out of those groups.
2) Use an In-built Role or Create a new Custom Role
You can either use any of the built-in Intune roles or create a new custom role as per your requirement. For demonstration purpose, I will be using an in-built role called Help Desk Operator and assign this role to London Help Desk and Paris Help Desk with their respective scope tags.
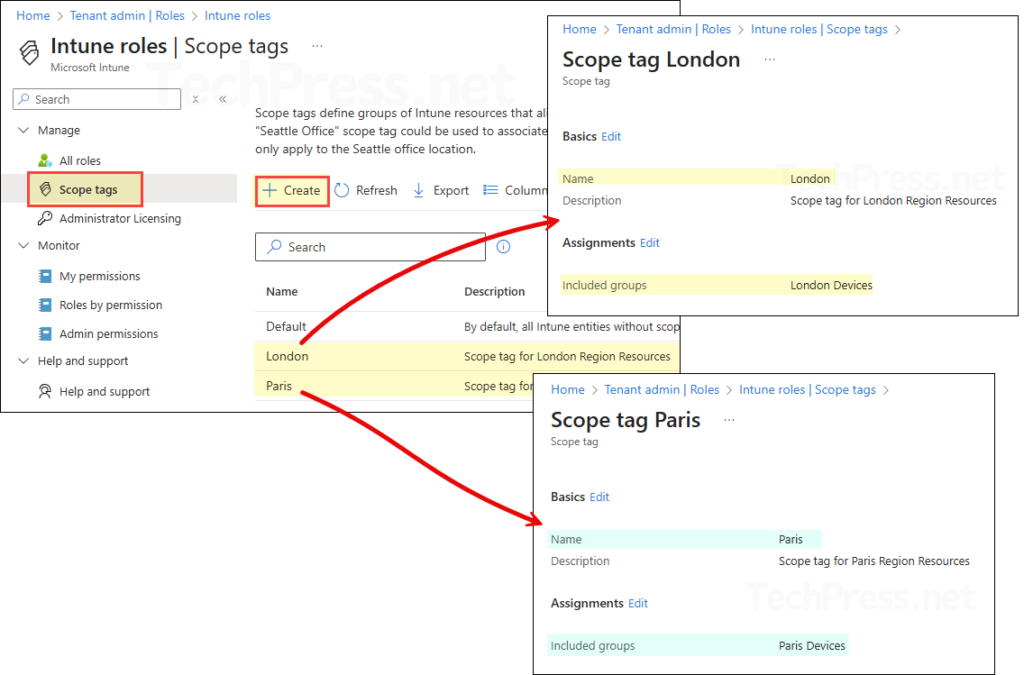
3) Role assignments
Assign the Help Desk Operator role to the London Help Desk and Paris Help Desk groups. When you create each role assignment, make sure to add the scope tag for the corresponding region. I have configured the assignments as shown in the table below. Scope (groups) lets you further restrict where the role can operate, so you can add specific groups that the help desk members are allowed to manage. For demonstration purposes, I used All users and All devices, combined with the appropriate scope tag.
| Role | Admin group (Members) | Scope (groups) | Scope (tags) |
|---|---|---|---|
| Help Desk Operator | London Help Desk | All Users, All Devices | London |
| Help Desk Operator | Paris Help Desk | All Users, All Devices | Paris |
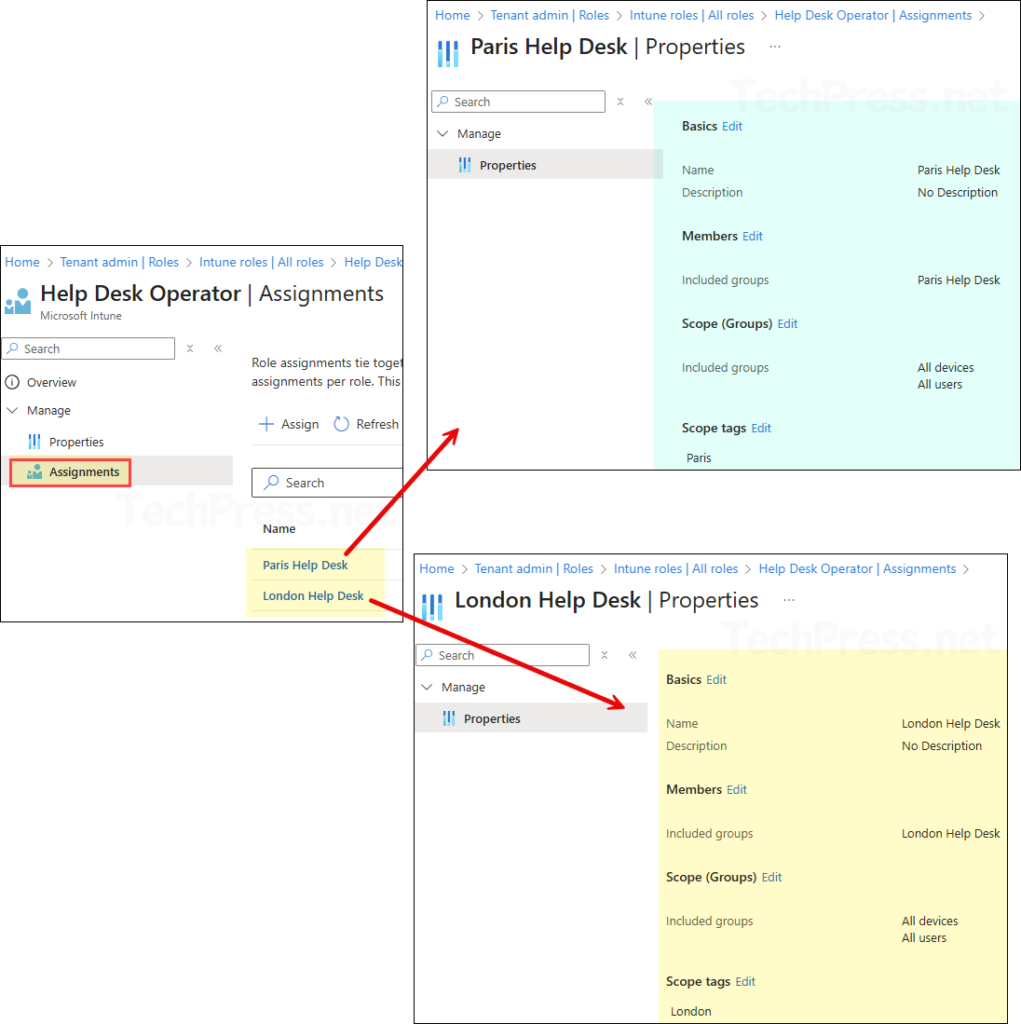
End Result
- Members of London Help Desk Entra security group can perform only the allowed actions on London Devices, and they can see only objects (policies, apps, scripts, etc.) tagged with London. Paris Admins get the same, limited to Paris.
- When members of these groups create new objects, the tag from their role assignment is applied automatically to the object, so it stays in-region.
London Help Desk User Experience
Now that we’ve created the scope tag, set up the role assignment, and assigned the Help Desk Operator role to the London Help Desk Entra group, any member of that group will see only the objects tagged with scope tag London and will have only the permissions allowed by the Help Desk Operator role.
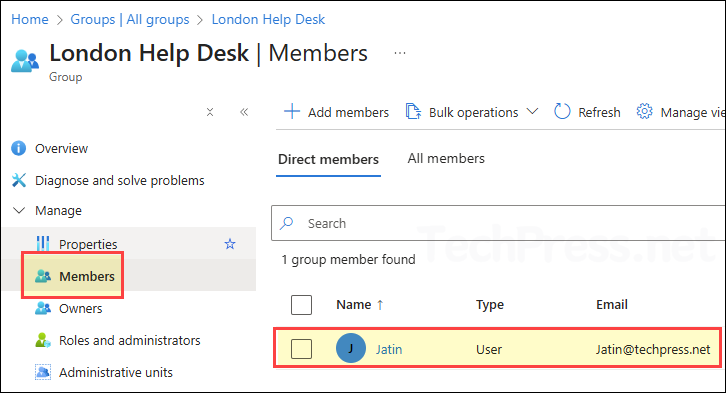
Below screenshot shows the membership of London Help Desk group and currently a user, [email protected] is a member of the group. Let’s sign in to Intune admin center as [email protected] and check the experience.
Since the London scope tag is applied to the London Devices group, which currently contains only one device (TECHPRESS-W-4), user [email protected] will see only this device under All Devices. In contrast, an Intune Administrator or Global Administrator would see all devices in the tenant.
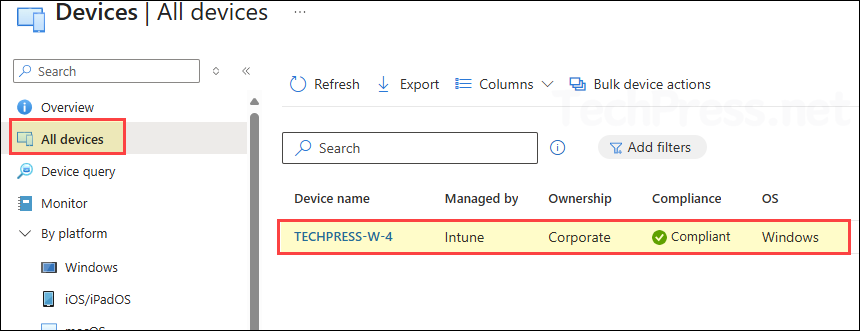
When you click on the device TECHPRESS-W-4 and open the Properties page, you’ll see that the London scope tag has been applied automatically. This confirms that the device inherited the tag from the London Devices group scope tag assignment, ensuring that only admins with the London scope tag in their role assignment can view and manage it.
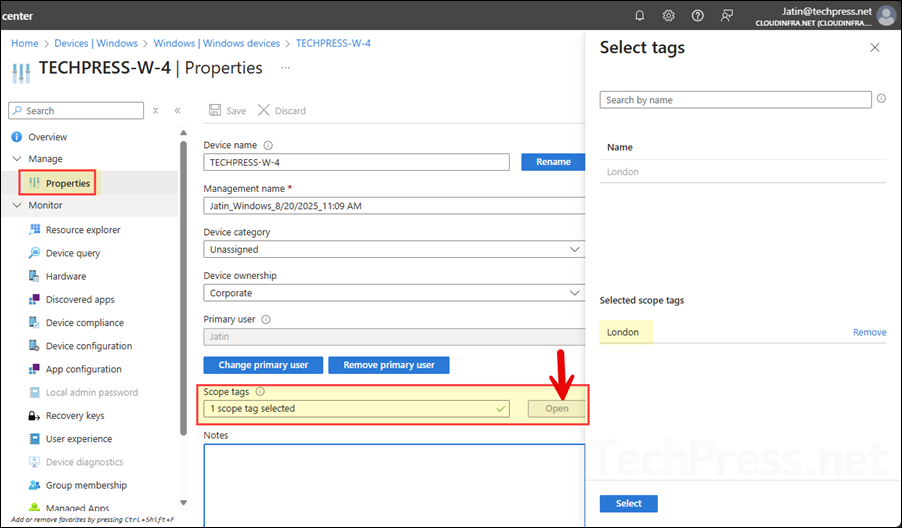
Now, let’s navigate to Intune admin center > Devices > Configuration to review the visible profiles. Since we applied the London scope tag to one of the device configuration profiles, this is the only profile that the user can see. All other profiles without the London tag remain hidden from this user’s view.
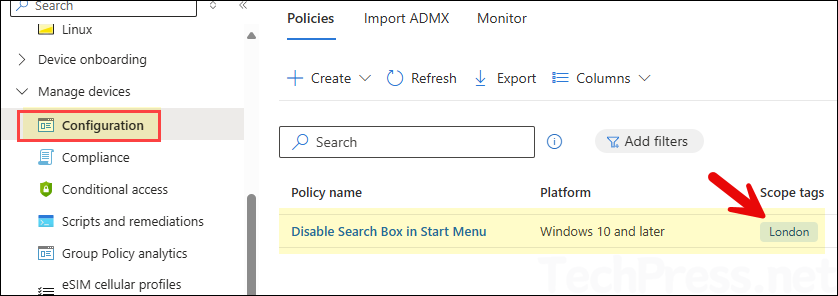
London Help Desk user is limited to the permissions defined in the Help Desk Operator role. Since this role does not include the ability to delete objects in Intune, the user cannot remove configuration profiles. When the user opens the tagged configuration profile, Delete option is visible but greyed out, confirming that they do not have permission to perform this action.
A user in the Paris Help Desk Entra security group will have a similar experience. This demonstrates how scope tags and RBAC roles work together and the benefits of a least-privilege model.
Best Practices
- Scope tags control what admins see and manage; they do not deploy policy. Continue to use group assignments for deployment.
- Keep tag names clean and concise (Region, Business Unit or Environment like Prod, Staging, Dev) etc.
- Prefer auto-scope on tags instead of manually tagging devices.
- If an admin role assignment has no scope tags, that assignment can see all objects it has permission for.
- Objects with the built-in Default tag may be hidden from region-scoped admins. Retag or include “Default” where appropriate.
- Exclusions & RBAC: If your policy/app uses Exclusion groups, ensure those groups are listed in the role’s Scope (groups) (or nested), otherwise scoped admins might not see the assignment as expected.
Assign Scope Tag Manually vs. Automatically
Now that we have concluded the demonstration part on Scope tags, I will now provide guidance on if the scope tag should be applied manually or automatically.
- Automatic Scope tag assignment: This is the preferred way to assign scope tags: use automatic assignment by linking a scope tag to a Microsoft Entra security group, ideally a dynamic device group. For example, assign the London scope tag to the London Devices dynamic Microsoft Entra security group. All devices in that group will automatically inherit the London scope tag. Please note that auto scope will overwrite manual tagging.
- Manual Scope tag assignment: You can go to the Intune admin center > Devices > All devices. Select a Device and go to Properties to assign a scope tag manually.
Scope Tag Troubleshooting Checklist
We always ensure that all the policies, roles, assignments are setup correctly, but the outcome is still not as expected. If you have setup scope tags correctly and still have issues, follow below guidance to resolve the issue.
- Check role assignmetns: Confirm if a user is a member of the correct Entra security group assigned to the role.
- Check Scope (groups): Verify that Scope (groups) include the devices (and users) you want these admins to manage. For a quick test, temporarily add All users and All devices to the assignment and see if visibility returns. If it does, the issue is with your Scope (groups) configuration. Review the group type (Security), membership, and any dynamic rules.
- Check Scope tags: Sign in to Intune admin center as Intune administrator or Global administrator and confirm if the scope tag is applied to the object as per the Scope tag assignment. For example, London or Paris scope tag as per our scenario.
- Confirm Device membership for tagging: Check the scope tag’s assignment group and verify that the device appears as a member. If it doesn’t, the device likely doesn’t meet the dynamic membership rule and therefore won’t receive the tag. Review the rule logic and the device’s attributes (ownership, OS, model, enrollment profile), then re-evaluate the group. For a quick check, add the device as a direct member to confirm visibility.
- Tagged Object Visibility Issue? If you have setup everything correctly and still users are not able to see the tagged objects. Check if the role provides at least read permission for the object. For example: Managed Devices – Read, Device configuration – Read permission etc.
- Permission Issue?: If its not an object visibility issue but an issue with users permission, then check the role permissions. For example, In our scenario we have used Help Desk operator role which does not have permission to delete an object in Intune.
- Session or Cache Issue: Sign out and sign back in to Intune admin center using Inprivate mode or Incognito mode of the browser to check if this resolves the issue.
- Object Supports Scope tag? Some items do not support scope tags like Windows Autopilot devices, Device compliance locations, Jamf devices and Corp device identifiers.
FAQs
Do I need scope tags if everyone is an Intune Admin?
Not for visibility, Intune Service/Global Admins see everything. Tags help when you use RBAC for delegation.
Can I use tags to target deployments?
No. Use Entra security groups for assignments; tags only control what scoped admins see/manage.
How many tags can I add?
Up to 100 per role assignment and per object.
Do VPP apps inherit tags?
Yes, VPP apps/ebooks inherit tags from their VPP token.
Conclusion
In this blog post, you have learnt about Scope tags and its implementation. Scope tags, combined with Intune RBAC, give you a clean and scalable way to delegate administration with least privilege. Plan a simple tag taxonomy, create the tags, auto-scope them to the right device groups, and tag your objects. Then assign roles to Entra security groups with the correct Scope (groups) and Scope tags so each team sees only what they should and can act only where they should.
