This post will demonstrate the steps to create custom attributes for macOS using Intune. Custom attributes let you collect the inventory data from Intune managed Macs by running a small shell script and saving its output back to Intune (For example: FileVault status, last reboot time, number of local admins, etc.). You create a Custom attribute policy, upload a script that echoes a single value, assign it to devices or users, and then read the results in Intune.
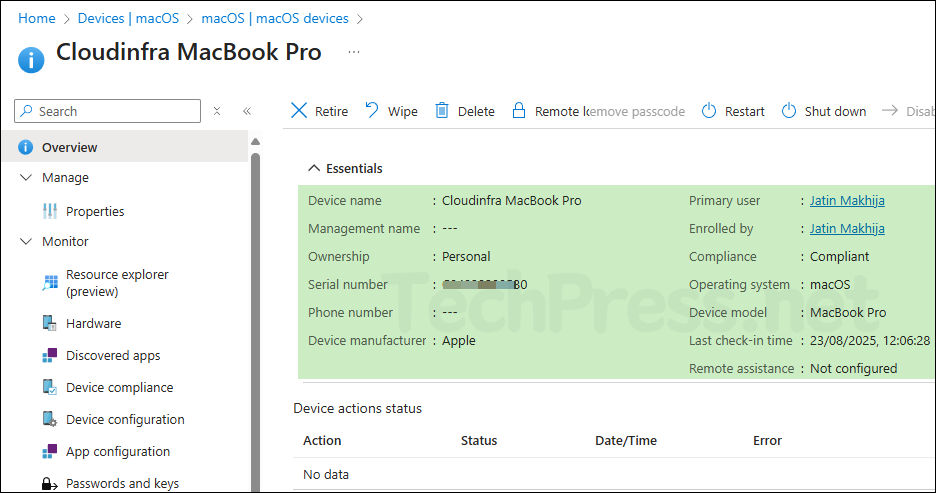
By default, Intune collects standard hardware and OS details for managed Macs. You can view this in the Intune admin center > Devices > macOS, then select any managed device. If you need more inventory data, such as battery condition, processor and memory details, or the last boot time across all Macs, use Custom attributes with a lightweight shell script.
In the next sections, I’ll show how to use Intune Custom attributes for macOS to gather advanced inventory that does not appear in the standard device view. Below is a list of standard details available for a Mac device on Intune admin center.
- Device name
- Management name
- Ownership
- Serial number
- Phone number
- Device manufacturer
- Primary user
- Enrolled by
- Compliance
- Operating system
- Device model
- Last check-in time
- Remote assistance
Contents
Prerequisites
- macOS devices are enrolled in Intune and running macOS 12 or later.
- Microsoft Intune management agent is installed (Intune deploys it automatically for macOS scripting).
- Devices must be able to reach the internet directly (proxy isn’t supported for the scripting agent).
- Your admin account has Device configuration rights (e.g., Intune Policy and Profile Manager role). Create Custom role in Intune.
- Shell scripts begin with
#!and must be in a valid location, such as #!/bin/sh or #!/usr/bin/env zsh. Deploy Shell Scripts Using Intune.
How Custom Attributes Work?
- You upload a shell script (sh/zsh) on Intune.
- The script must
echoexactly one value (no labels, no extra logging). - You choose the data type for the attribute: String, Integer, or Date.
- If you select Date, the script must output an ISO-8601 timestamp (shown in next section).
- Script output size must be ≤ 20 KB.
- Intune runs custom-attribute scripts on managed Macs every ~8 hours and records the result.
After you have created a custom attribute shell script, test it on a Mac device locally using Terminal, It should print only the value and exit 0.
Step1: Prepare the Custom Attribute Script
Create a custom attribute shell script to fetch the particular inventory data from Mac devices. Below is a small example script which will get the last boot time value of all managed mac devices and save the value in Intune.
Copy below script code and save it as Last_Boot_Time.sh (you can use any filename, but the extension must be .sh or .zsh).
Microsoft provides many custom attribute scripts in the GitHub Intune samples, download them and use it to fetch the data as per your requirement: Custom Attributes at master · microsoft/shell-intune-samples · GitHub. You can check my GitHub page for more pre-made Custom attributes scripts: Jatin-Makhija-sys/Powershell-Scripts · GitHub.
Last_Boot_Time.sh
#!/bin/zsh
# Prints the last boot time in ISO-8601 UTC (Date type)
boottime_epoch=$(sysctl -n kern.boottime | awk -F'[ ,]' '{print $4}')
date -u -r "${boottime_epoch}" +"%Y-%m-%dT%H:%M:%SZ"Step 2: Deploy the Custom Attribute Script
- Sign in to the Intune admin center > Devices > macOS > Custom attributes for macOS > click Create.
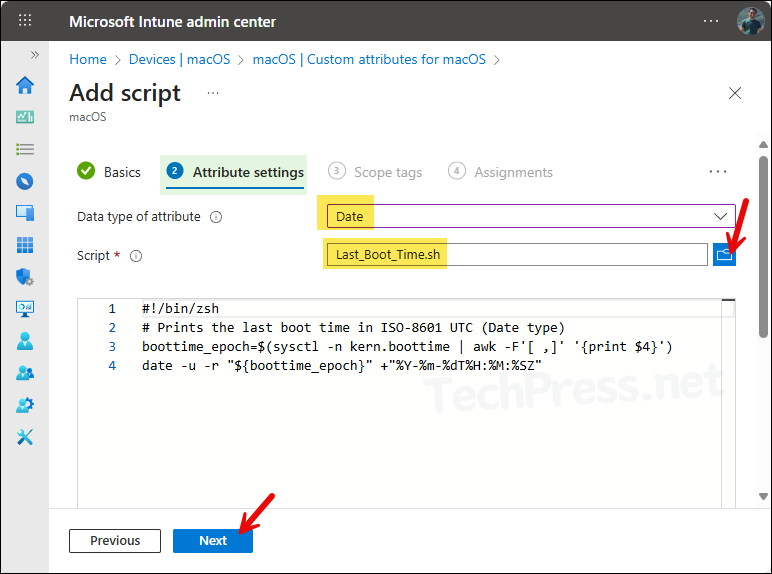
- Basics tab: Provide a Name and Description of the policy. For example: Last Boot Time record.
- Attribute settings:
- Data type of attribute: There are three values in the drop-down String, Integer, and Date. Select the value to match with the output of your script. For example, If your custom attribute shell script is returning a Date, then select date as the type of the attribute.
- Script: Browse the script file using the blue folder icon and click Next.
- Scope tags (optional): This is an optional configuration, skip it by clicking on Next. A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them.
- Assignments: Create or use an entra security group containing macOS users or devices. Click on Add groups and select the group to assign this policy.
- Review + Add: Review the deployment summary and Click on Add.
That’s it, Custom attributes for macOS script is created. You can view all your Custom attributes scripts under Devices > macOS > Custom attributes for macOS.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitor Custom Attribute Script Status
- Go to Devices > macOS > Custom attributes for macOS.
- From the Overview page, check if the status is Succeeded or there is an Error.
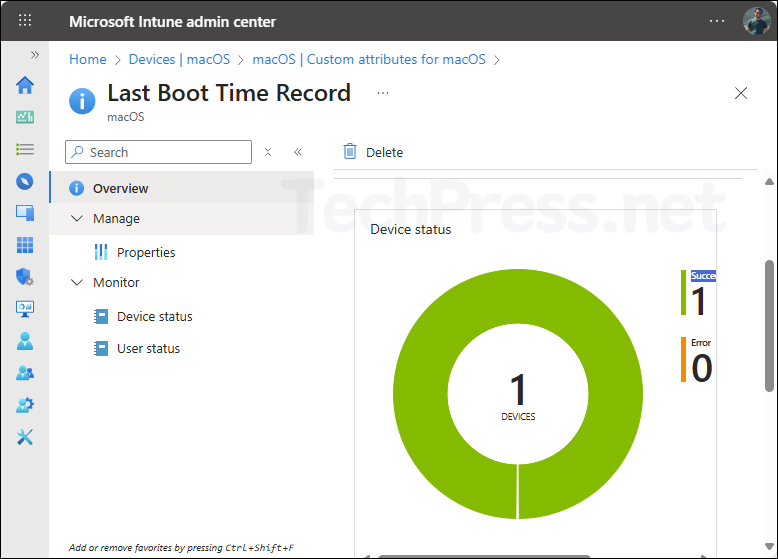
Check Custom Attributes Script Result
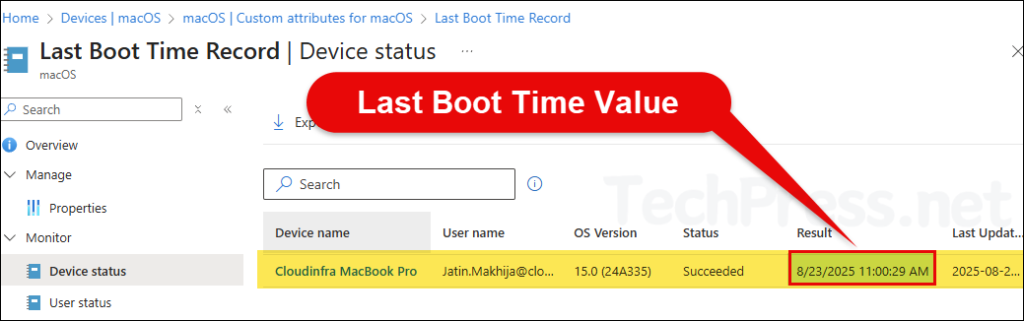
You can check and confirm the return value of Custom attributes script from Intune admin center. In our example scenario, we deployed a script to get the last boot time value of macOS computers. Let’s check how to find this value.
- Sign in to the Intune admin center > Devices > macOS > Custom attributes for macOS.
- Click on your Intune deployment and go to Device status. Check under the Result column, which will show the script return value.
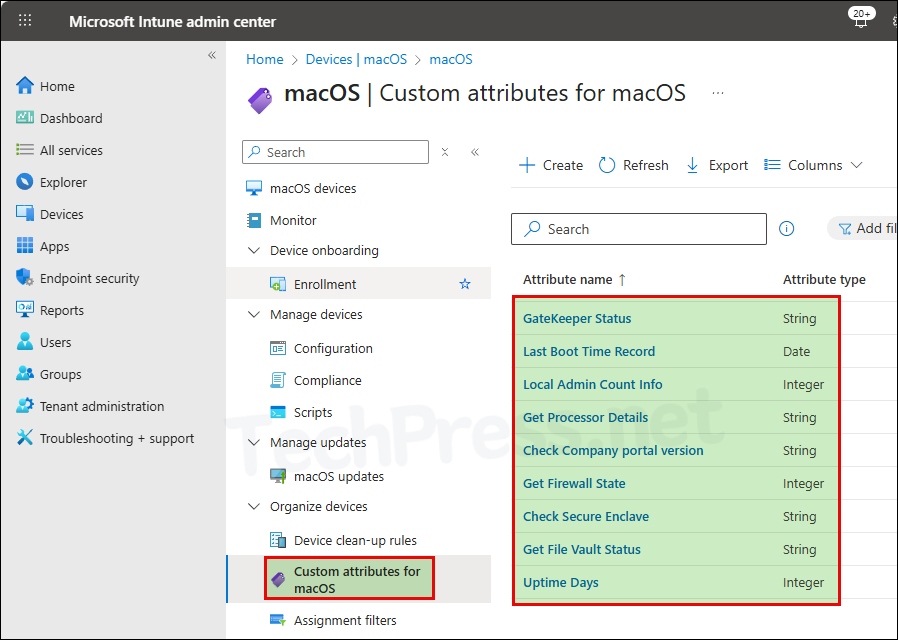
Deploy More Custom Attributes Shell Scripts
You can deploy more custom attributes scripts and get the inventory information as per your requirements. Ensure that the correct Attribute type is selected for the deployment. More Scripts.
| Attribute Name | Script File | Data Type | Example Output |
|---|---|---|---|
| FileVault status | 01_filevault_status.zsh | String | On |
| Bootstrap Token escrowed to MDM | 02_bootstrap_token_escrowed.zsh | String | YES |
| Rosetta installed (Apple Silicon) | 03_rosetta_installed.zsh | String | Yes |
| Battery cycle count | 04_battery_cycle_count.zsh | Integer | 241 |
| Local admin count | 05_local_admin_count.zsh | Integer | 3 |
| Gatekeeper (App assessment) | 06_gatekeeper_status.zsh | String | Enabled |
| macOS Firewall state | 07_firewall_state.zsh | Integer | 1 |
| Secure Enclave present | 08_secure_enclave_present.zsh | String | Yes |
| Company Portal version | 09_company_portal_version.zsh | String | 5.2409.0 |
| Uptime (days) | 10_uptime_days.zsh | Integer | 12 |
Troubleshooting
For troubleshooting custom attribute script related issues, you can read the log files to investigate. Refer to IntuneMDMDaemon*.log and IntuneMDMAgent*.log files, which could provide useful information for troubleshooting and finding out the root cause of the issue. For more information about how to locate these files on a macOS device, see my other blog post, Collect Intune Logs from macOS Devices.
