In this blog post, I will demonstrate the steps to configure password history policy using Intune. This policy specifies the number of passwords stored in the device’s password history database that cannot be reused. By default, this value is 0, it means storage of previously used passwords is not required and during password reset, users are allowed to use any of the previously used passwords.
Setting a value of DevicePasswordHistory of greater than 0 enables this policy and will not allow users to use a password from device password history.
Allowing users to reuse the same passwords over an extended period can pose security risks, making it easier for attackers to guess the password. A lower value of DevicePasswordHistory means that the system remembers fewer passwords, allowing users to reuse old passwords multiple times.
Configuring a higher value for this setting ensures that users cannot repeatedly reuse the same passwords. While you can set the DevicePasswordHistory value up to 50, the maximum supported value is 24. Configuring a value greater than 24 will result in an error code 65000.
I will create a device configuration policy on Intune admin center and use below Settings catalog policy to configure device password history.
| Profile type | Category | Setting | Value |
|---|---|---|---|
| Settings Catalog | Device Lock | Device Password History | <provide a value> |
Contents
DevicePasswordHistory Policy CSP
The DeviceLock CSP includes a setting called DevicePasswordHistory, which allows you to specify the number of passwords that can be stored in the history and cannot be reused.
For example, a value of 1 indicates that the user cannot use their current password when setting up a new password. A value of 10 means the user cannot set their password to the current one or any of their previous 9 passwords.
DevicePasswordHistory Policy CSP URI
./Device/Vendor/MSFT/Policy/Config/DeviceLock/DevicePasswordHistory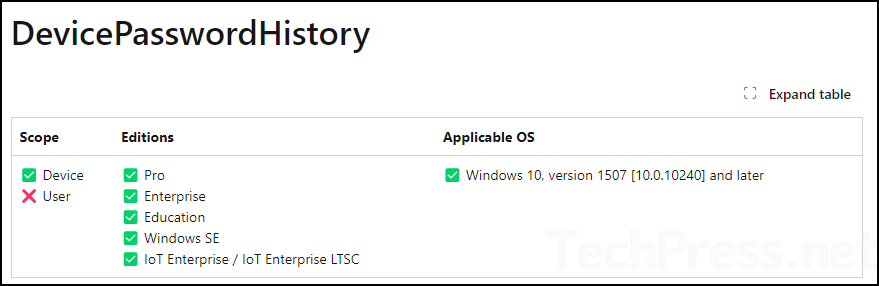
Create DevicePasswordHistory Intune Policy
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
- Platform: Windows 10 and later
- Profile type: Settings Catalog
- Basics Tab: Provide a Name and Description of the profile.
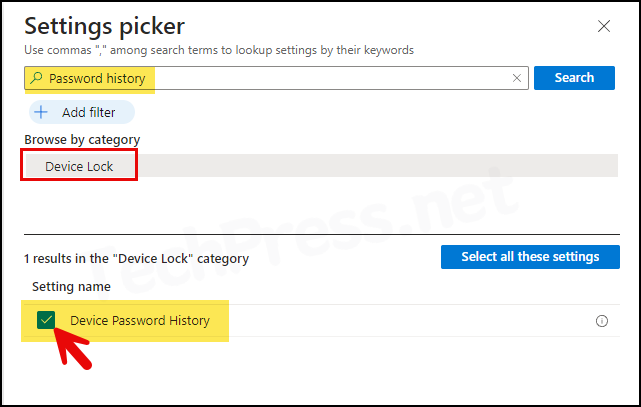
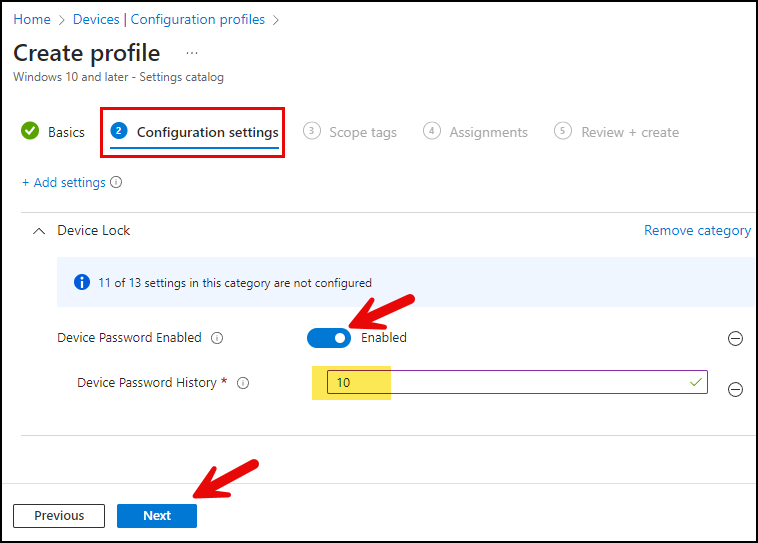
- Configuration settings: Click on + Add settings and then search for Password history in the settings picker. Select Device Lock category. Then select Device Password History.
- Use the toggle switch to enable the Device Password Enabled setting and set the Device Password History value. For example, if you set the Device Password History to 10, it means that 10 passwords will be remembered, and the user cannot use any of the last 10 passwords (including the current password) when changing the password.
- Scope tags: Click on Next.
- Assignments: Assign this profile to an Entra Security group containing users or devices. Click on Next to proceed.
- Review + create: Review the policy summary and click Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Another way to trigger the Intune device check-in process is by restarting the device.
Monitoring Deployment Progress
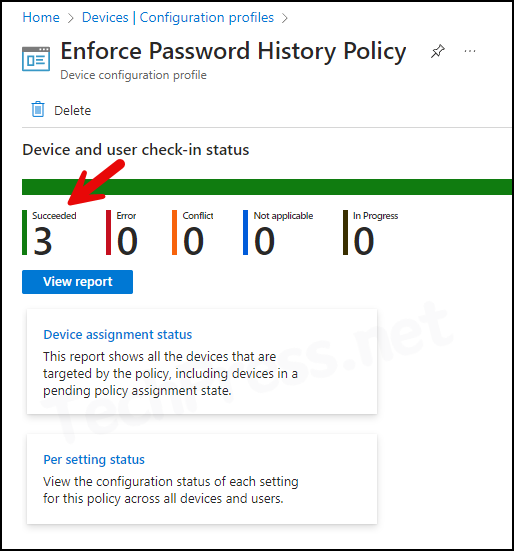
- Sign in to the Intune admin center > Devices > Configuration.
- Select the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
Verify DevicePasswordHistory Policy on Target Device
To confirm if the policy has been applied on the target devices, You can either review Event Viewer logs, or you can use the Windows Registry Editor. Let’s explore both these methods:
1. Check Event Viewer Logs
- Press the Windows key + R to open the Run dialog box.
- Type
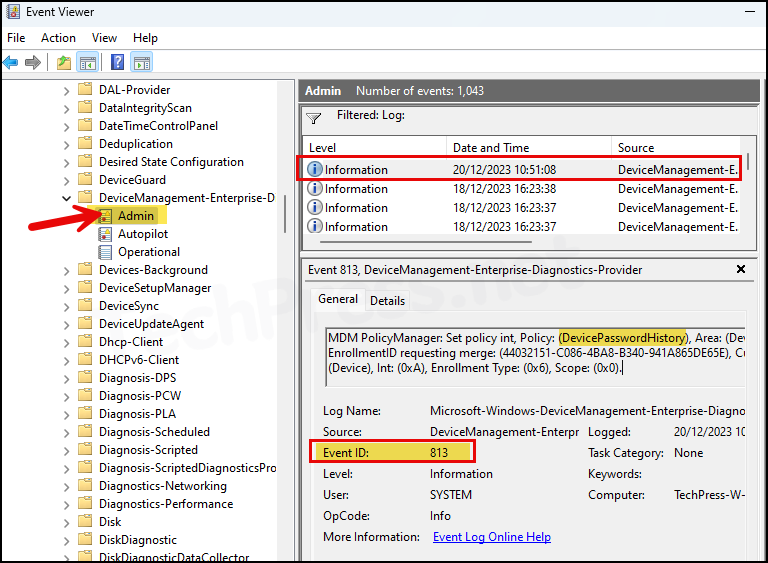
eventvwrand Enter to open the Event viewer console. - Go to Application and Services logs > Microsoft > Windows > Devicemanagement-Enterprise-Diagnostics-Provider > Admin folder.
- Search for Event ID 813 or 814 and go through the logs to find the one related to the deployment.
2. Check Registry Editor
You can also verify the DevicePasswordHistory registry entry, which is created after deploying this policy via Intune. To confirm, follow these steps:
- Press the Windows key + R to open the Run dialog box.
- Type
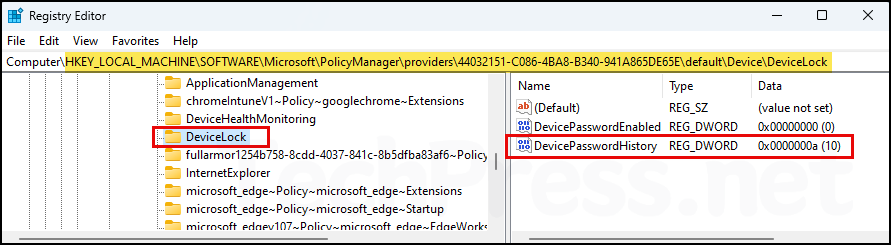
regeditand Enter to open the Registry Editor. - Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\<GUID>\default\Device\DeviceLock.
- On the right-hand side, locate a registry entry called DevicePasswordHistory. The value of this entry has been configured to 10 as per the Intune policy.
To easily find DevicePasswordHistory registry entry, navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\ location. Right-click on the providers folder and search for the keyword DevicePasswordHistory.
Tip
Troubleshooting
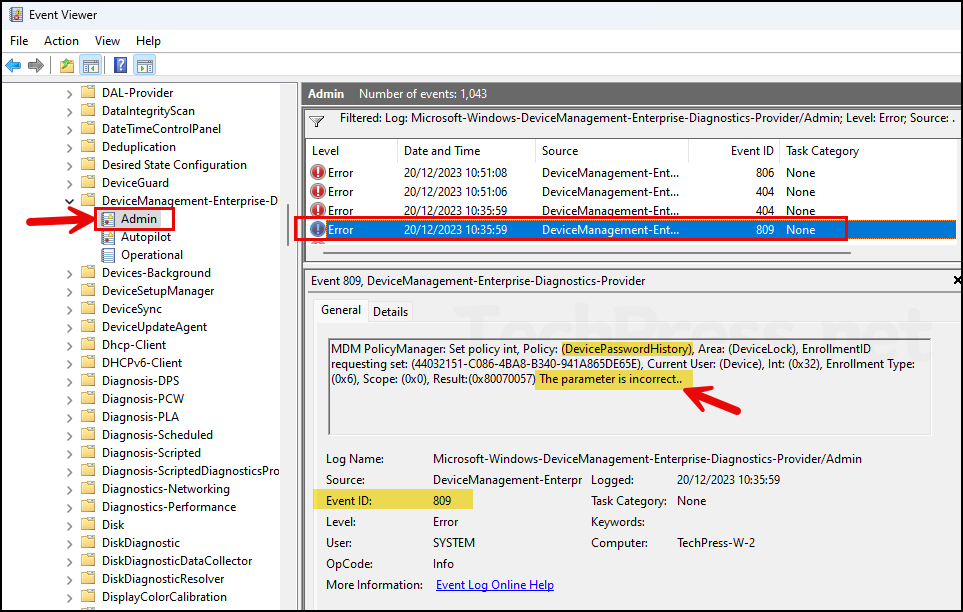
After configuring and deploying the policy using Intune, it may not be successfully applied. You might encounter Error Code, 65000 in the Intune admin center, and while checking Event Viewer logs on the target device, you may see Event ID 809.
Since the error indicates that the parameter is incorrect, it suggests that the value configured for DevicePasswordHistory is not supported. Try using a different value between 1 and 24 and check again.
MDM PolicyManager: Set policy int, Policy: (DevicePasswordHistory), Area: (DeviceLock), EnrollmentID requesting set: (44032151-C086-4BA8-B340-941A865DE65E), Current User: (Device), Int: (0x32), Enrollment Type: (0x6), Scope: (0x0), Result:(0x80070057) The parameter is incorrect..