In this blog post, I’ll show you how to check Gatekeeper status on macOS using Intune. Gatekeeper protects Macs by assessing apps at launch. It allows apps to run only if they’re from the App Store or trusted developers and typically Apple-notarized.
You can easily check the Gatekeeper status using a Custom attributes shell script. This script will query gatekeeper status and sends the value to Intune. For more information about creating a custom attribute, refer to my other detailed step-by-step guide on creating Custom Attributes using Intune.
Refer to the step-by-step guide to learn about shell script deployment on macOS using Intune: Deploy Shell Scripts On MacOS Using Intune.
Contents
Step 1: Download CheckGatekeeperStatus.zsh Script
Download the shell script from Microsoft GitHub repo: CheckGatekeeperStatus.zsh. We will use this script to create Intune deployment in the next step.
CheckGatekeeperStatus.zsh
#!/bin/zsh
#set -x
############################################################################################
##
## Extension Attribute script to check Gatekeeper status
##
############################################################################################
## Copyright (c) 2020 Microsoft Corp. All rights reserved.
## Scripts are not supported under any Microsoft standard support program or service. The scripts are provided AS IS without warranty of any kind.
## Microsoft disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a
## particular purpose. The entire risk arising out of the use or performance of the scripts and documentation remains with you. In no event shall
## Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever
## (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary
## loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility
## of such damages.
## Feedback: [email protected]
# Fixed variables
gatekeeper=$(spctl --status)
notcompliance="assessments disabled"
# Attempt to chexk status of Gatekeeper and return it's result
if [[ "$gatekeeper" == "$notcompliance" ]]; then
echo "Gatekeeper is not enabled."
else
echo "Gatekeeper is enabled."
fiStep 2: Deploy CheckGatekeeperStatus.zsh Script
Next, we will deploy CheckGatekeeperStatus.zsh script using Intune admin center. Let’s check the steps:
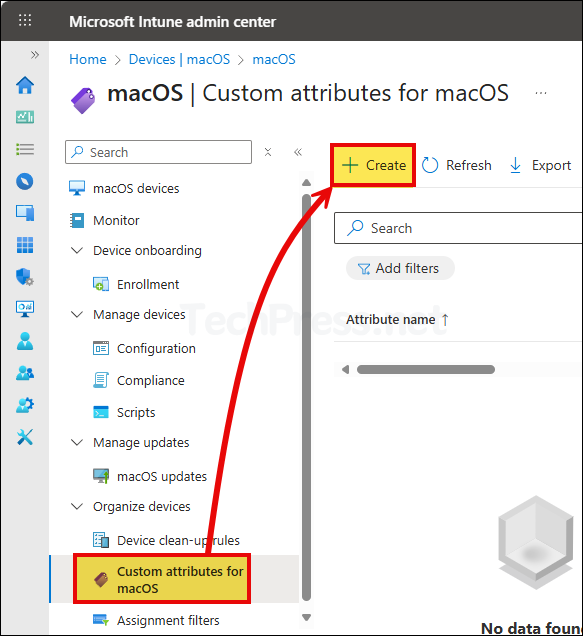
- Sign in to the Intune admin center > Devices > macOS > Custom attributes for macOS > click Create.
- Basics tab: Provide a Name and Description of the policy. For example: Check Gatekeeper Status.
- Attribute settings:
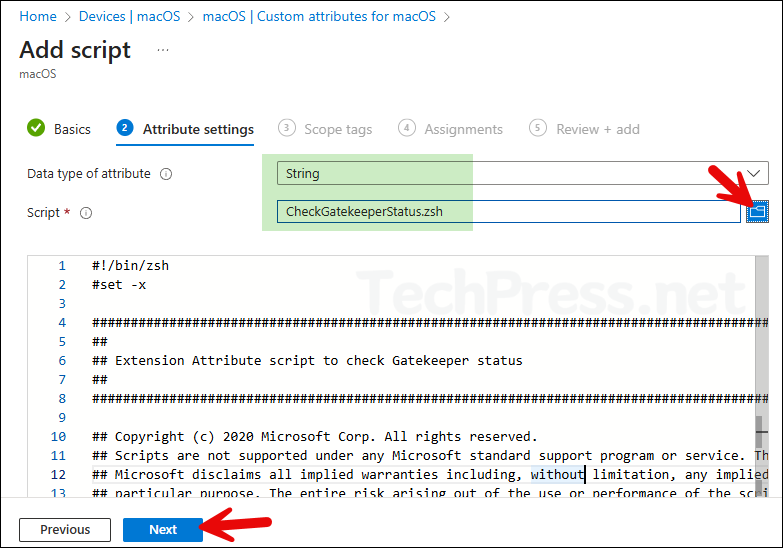
- Data type of attribute: There are three values in the drop-down String, Integer, and Date. Select the value to match with the output of your script. Our Gatekeeper shell script returns String value as output. Therefore, we will select String.
- Script: Browse the script file using the blue folder icon and click Next.
- Scope tags (optional): This is an optional configuration, skip it by clicking on Next. A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them.
- Assignments: Create or use an entra security group containing macOS users or devices. Click on Add groups and select the group to assign this policy.
- Review + Add: Review the deployment summary and Click on Add.
That’s it, Custom attributes for macOS script is created. You can view all your Custom attributes scripts under Devices > macOS > Custom attributes for macOS.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitor Gatekeeper Custom Attribute Script Status
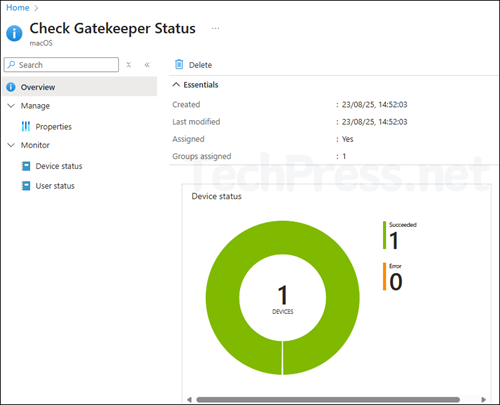
- Go to Devices > macOS > Custom attributes for macOS.
- From the Overview page, check if the status is Succeeded or there is an Error.
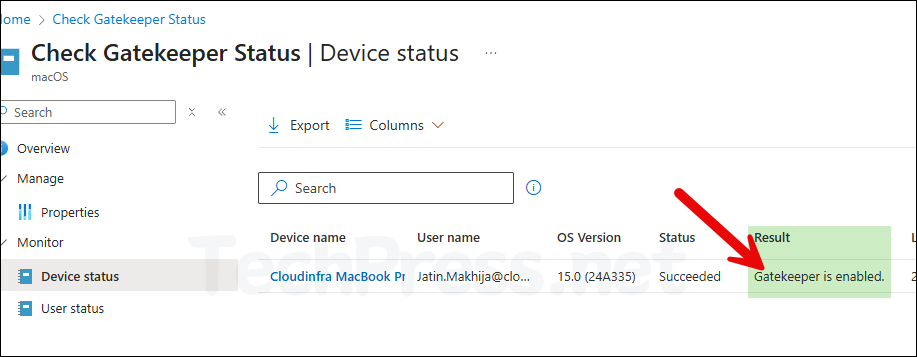
Gatekeeper Custom Attribute Script Result
You can check and confirm the return value of Custom attributes script from Intune admin center. In our scenario, we deployed a script to check Gatekeeper status on macOS computers. Let’s check how to find this value.
- Sign in to the Intune admin center > Devices > macOS > Custom attributes for macOS.
- Click on your Intune deployment (Check Gatekeeper Status) and go to Device status. Check under the Result column, which will show the script return value.
Troubleshooting
For troubleshooting custom attribute script related issues, you can read the log files to investigate. Refer to IntuneMDMDaemon*.log and IntuneMDMAgent*.log files, which could provide useful information for troubleshooting and finding out the root cause of the issue. For more information about how to locate these files on a macOS device, see my other blog post, Collect Intune Logs from macOS Devices.
