In this post, I will show you how to connect to Microsoft Graph using Get-MsalToken. Get-MsalToken is the simplest way to fetch an OAuth 2.0 access token for Microsoft Graph directly in PowerShell using the MSAL.PS module. It works for user-delegated and app-only scenarios, including interactive, device code, client secret, and certificate flows.
Once you have the token, pass it in an Authorization header for REST calls or supply it to Connect-MgGraph with -AccessToken switch. Using Get-MsalToken to connect to Microsoft Graph PowerShell is just one of connection method. For other ways to connect with Graph PowerShell, refer to the guide: How to Use Connect-MgGraph PowerShell cmdlet.
Contents
Prerequisites
- PowerShell 7.x or Windows PowerShell 5.1
- MSAL.PS module
- An Entra ID tenant ID and an app registration.
Install MSAL.PS PowerShell Module
To work with Get-MSALToken cmdlet, you will have to install MSAL.PS module. Open PowerShell console on your device and run below commands to install and import the module. Last command (Get-Command Get-MsalToken -Syntax) is for checking all the switches you can use with Get-MsalToken and also to verify if it’s working fine.
Install MSAL.PS module
#Install or update the module
Install-Module MSAL.PS -Scope CurrentUser -Force
#Import the module
Import-Module MSAL.PS
# Get all switches/parameters of Get-MsalToken cmdlet
Get-Command Get-MsalToken -Syntax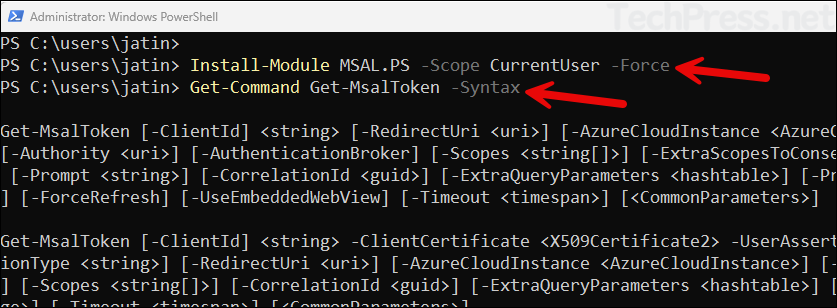
Create an App Registration in Entra
Get-MsalToken requires an app registration in the Entra admin center. Create the app and assign the required API permissions, then use Get-MsalToken to obtain an access token and connect to Microsoft Graph.
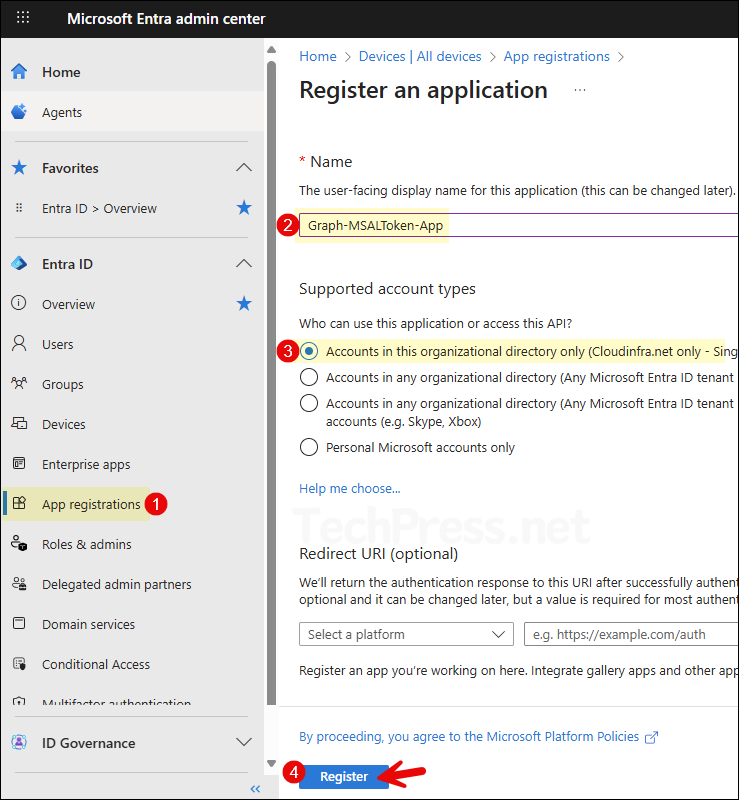
- Sign in to the Entra admin center > Expand Entra ID > App registrations. Click on + New registration.
- Provide a Name of the app and select the Supported account types. I have given a name of the app as Graph-MSALToken-App and selected Accounts in this organization directory only. Leave the Redirect URI as blank.
If you get AADSTS500113: No reply address is registered for the application error when trying to get the access token using Get-MsalToken, then you have to configure Redirect URI and try to connect again. I have explained about this issue and how to fix it at the end of the post.
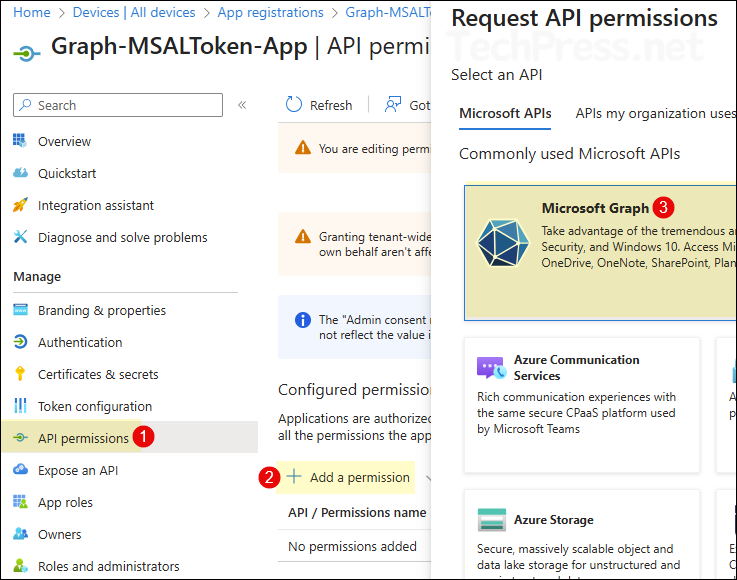
- After the app is created, you’ll find it listed under App registrations. Open the app, then go to API permissions > + Add a permission, and select Microsoft Graph.
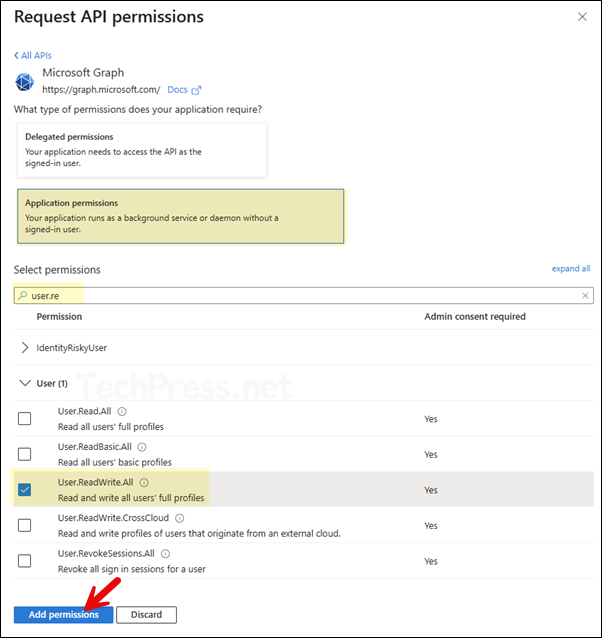
- Select Application permissions and search for the permissions you want to add to this app. Select the requirement permissions and once all the permissions are selected, click on Add permissions.
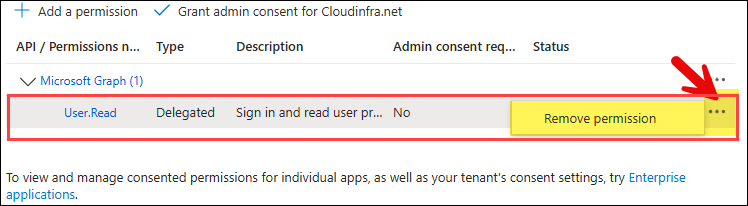
- This is an optional step to remove the default User.Read delegated permission. If you do not require this default API permission, then click on ellipses (..) and remove it
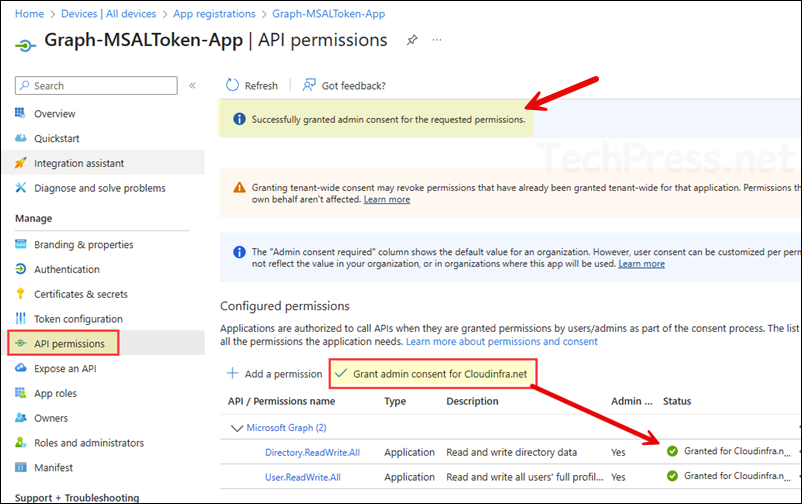
- You must grant admin consent for the API permissions added to the app. To do this, click Grant admin consent for <your org>. Once consent is granted, the status column will show a green check for each permission.
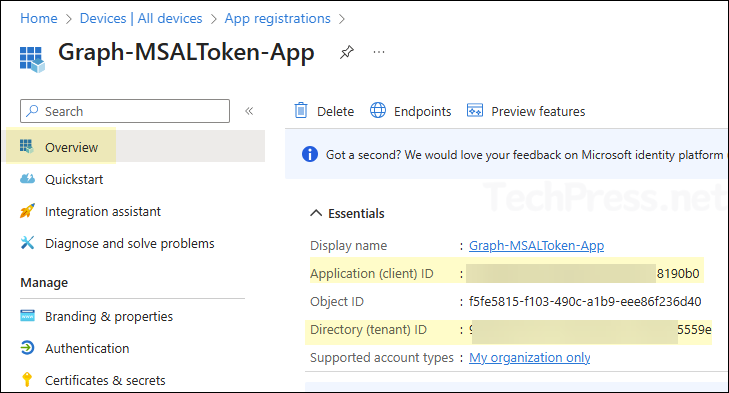
Copy Client ID and Tenant ID
Copy the client ID and tenant ID information from the app registration overview page. This will be required to get the access token and establishing a connection with graph. Save it somewhere in a notepad for easy access.
Connect to Graph PowerShell via Get-MsalToken Access Token
There are several ways to get an access token using the Get-MsalToken cmdlet.
- App-only method
- Device code flow
- Using Client secret
- Using Certificate
1. Get App only Access Token
You can obtain an app-only access token using below PowerShell script and then use that token to establish a connection to Microsoft Graph PowerShell with Connect-MgGraph. You can also use REST API to establish the connection. I have provided the PowerShell code snippet for both.
Use the tenant ID and client ID you noted earlier and update the script before running it. Optionally, you can include delegated permissions by using the -Scopes parameter. Once the session is established, you can perform a quick test using Get-MgUser.
Since the following script uses the Connect-MgGraph PowerShell cmdlet, you’ll need to install the Microsoft Graph PowerShell module on your computer before running it. To install the Microsoft Graph module on your system, refer to the step-by-step guide: How to Install Microsoft Graph PowerShell Module.
Install-Module Microsoft.Graph -Scope CurrentUser -Repository PSGallery -ForceApp only access token
$tenantId = "<YOUR_TENANT_ID_GUID>"
$clientId = "<YOUR_CLIENT_ID>"
$token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -Interactive
$token.AccessToken # view the access token
$secureToken = ConvertTo-SecureString $token.AccessToken -AsPlainText -Force
Connect-MgGraph -AccessToken $secureTokenExample 1
$tenantId = "9ccda47d-f87c-44dd-a9ee-5543g525359e"
$clientId = "fc74brr5-ge60-458c-bcfd-29c8718190b0"
$token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -Interactive
$token.AccessToken # view the access token
$secureToken = ConvertTo-SecureString $token.AccessToken -AsPlainText -Force
Connect-MgGraph -AccessToken $secureTokenExample 2
$tenantId = "9ccda47d-f87c-44dd-a9ee-5543g525359e"
$clientId = "fc74brr5-ge60-458c-bcfd-29c8718190b0"
$token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -scopes User.read.All -Interactive
$token.AccessToken # view the access token
$secureToken = ConvertTo-SecureString $token.AccessToken -AsPlainText -Force
Connect-MgGraph -AccessToken $secureTokenQuick test to confirm the connection
Get-MgUser -Top 5 | Select-Object Id, DisplayName, UserPrincipalName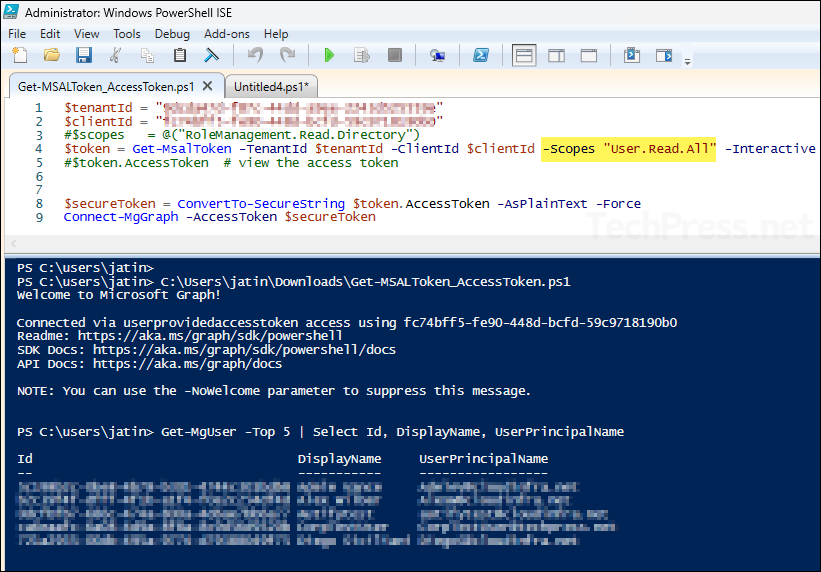
Use the Access Token with Microsoft Graph REST (Example 1)
$tenantId = "9ccda47d-f87c-44dd-a9ee-5543g525359e"
$clientId = "fc74brr5-ge60-458c-bcfd-29c8718190b0"
$token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -Interactive
$token.AccessToken # view the access token
$headers = @{ Authorization = "Bearer $($token.AccessToken)" }
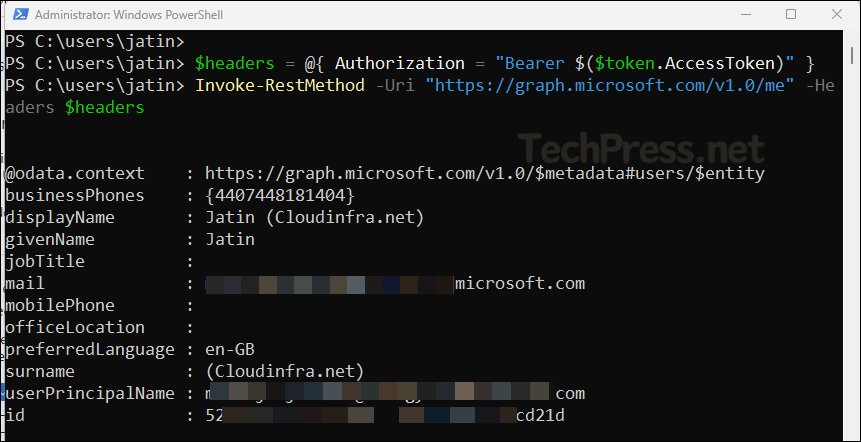
$me = Invoke-RestMethod -Uri "https://graph.microsoft.com/v1.0/me" -Headers $headers
$meUse the Access Token with Microsoft Graph REST (Example 2)
$tenantId = "9ccda47d-f87c-44dd-a9ee-5543g525359e"
$clientId = "fc74brr5-ge60-458c-bcfd-29c8718190b0"
$scopes = @("RoleManagement.Read.Directory")
$token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -scopes $scopes -Interactive
$token.AccessToken # view the access token
$headers = @{ Authorization = "Bearer $($token.AccessToken)" }
$me = Invoke-RestMethod -Uri "https://graph.microsoft.com/v1.0/me" -Headers $headers
$me2. Device code flow
When using the device code flow method, you’ll receive a code from the Get-MsalToken cmdlet. You can use this code in a web browser on the same device, or, if a browser isn’t available, open a browser on another device and go to https://microsoft.com/devicelogin, then enter the code to sign in.
Get-MsalToken with device code flow
$tenantId = "<YOUR_TENANT_ID_GUID>"
$clientId = "<YOUR_PUBLIC_CLIENT_APP_ID>"
$scopes = @("User.Read.All")
$token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -Scopes $scopes -DeviceCode
# You will see instructions and a code to enter at https://microsoft.com/devicelogin
$headers = @{ Authorization = "Bearer $($tok.AccessToken)" }
Invoke-RestMethod -Uri "https://graph.microsoft.com/v1.0/me" -Headers $headersExample
$tenantId = "9ccda47d-f87c-44dd-a9ee-5543g525359e"
$clientId = "fc74brr5-ge60-458c-bcfd-29c8718190b0"
$scopes = @("User.Read.All")
$token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -scopes $scopes -DeviceCode
# You will see instructions and a code to enter at https://microsoft.com/devicelogin
$headers = @{ Authorization = "Bearer $($token.AccessToken)" }
Invoke-RestMethod -Uri "https://graph.microsoft.com/v1.0/me" -Headers $headers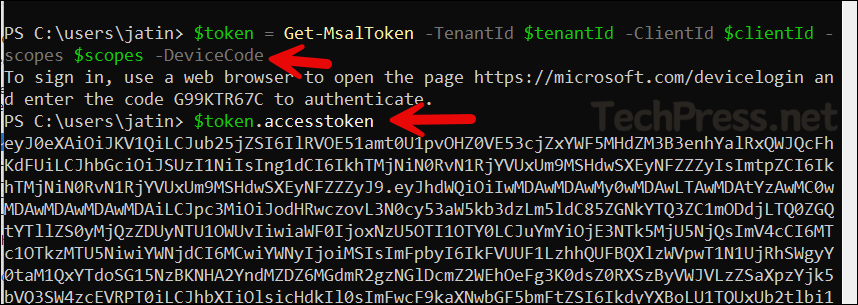
3. Using Client Secret
Use it for unattended scripts and ensure to keep the client secret in a secure place like Azure keyvault. Requires Application permissions on your app registration and admin consent. For this, Add Microsoft Graph Application permissions (for example User.Read.All), Grant admin consent and then create a client secret.
- Sign in to the Entra admin center > Expand Entra ID > App registrations. Click on the Graph-MSALToken-app app or the app registration you created.
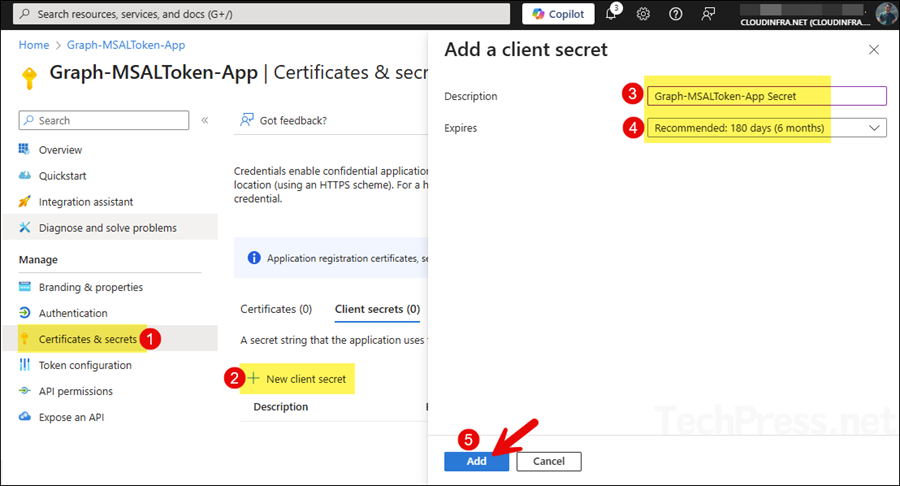
- Click on Certificates & secrets > + New client secret. Provide a description and expiry value, and then click on Add.
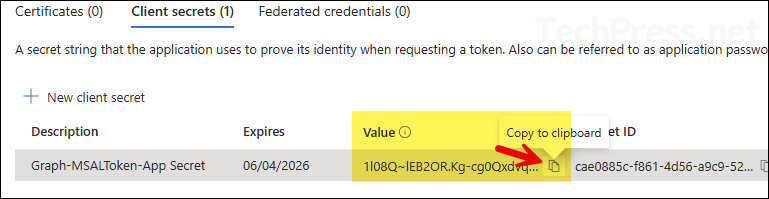
- Copy the client secret value immediately after creating it. The value is shown only for a short time, after that you will not be able to view or copy this value.
Get_MSALToken_ClientSecret.ps1
# Provide Client IDs, Tenant ID and Client secret
$TenantId = "9ccda47d-f87c-44dd-a9ee-5543g525359e"
$ClientId = "fc74brr5-ge60-458c-bcfd-29c8718190b0"
$ClientSecretPlain = "1l08Q~lEB2OR.Kg-cg0Qxdvqz~i8Zst~IJDHYbxV"
# MSAL Token Props
$msalParams = @{
TenantId = $TenantId
ClientId = $ClientId
ClientSecret = (ConvertTo-SecureString $ClientSecretPlain -AsPlainText -Force)
Scopes = "https://graph.microsoft.com/.default" # app-only = .default
}
$token = Get-MsalToken @msalParams
Connect-MgGraph -AccessToken (ConvertTo-SecureString $token.AccessToken -AsPlainText -Force)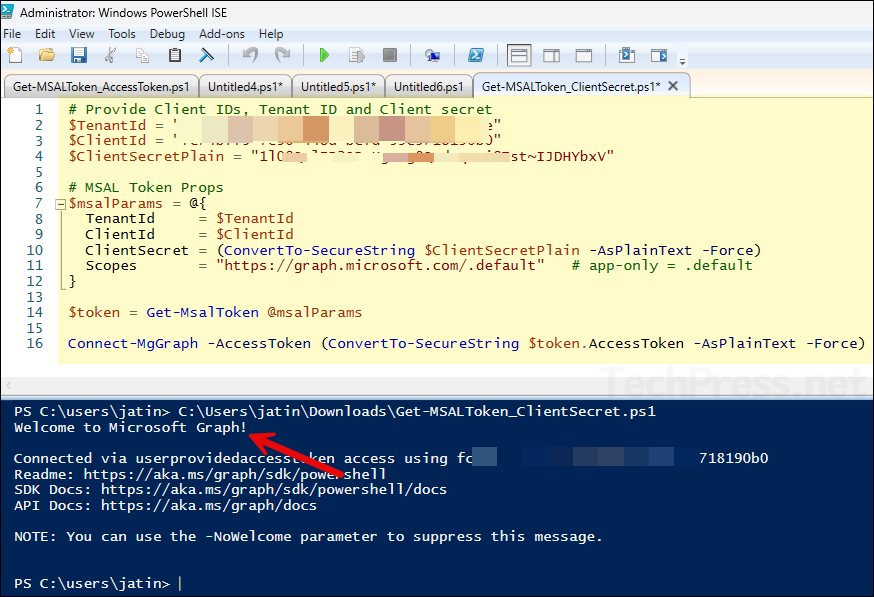
Get_MSALToken_ClientSecret_REST.ps1
# Provide Client IDs, Tenant ID and Client secret
$TenantId = "9ccda47d-f87c-44dd-a9ee-5543g525359e" #replace with your tenant ID
$ClientId = "fc74brr5-ge60-458c-bcfd-29c8718190b0" #replace with your client ID
$ClientSecretPlain = "1l08Q~lEB2OR.Kg-cg0Qxdvqz~i8Zst~IJDHYbxV" #replace with your client secret
# --- Get token (app-only => .default) ---
$msalParams = @{
TenantId = $TenantId
ClientId = $ClientId
ClientSecret = (ConvertTo-SecureString $ClientSecretPlain -AsPlainText -Force)
Scopes = "https://graph.microsoft.com/.default"
}
$token = Get-MsalToken @msalParams
# --- Build header ---
$headers = @{ Authorization = "Bearer $($token.AccessToken)" }
# --- Call Graph (requires Graph Application permission: User.Read.All + admin consent) ---
$req = @{
Uri = "https://graph.microsoft.com/v1.0/users?$top=5"
Headers = $headers
Method = "GET"
}
Invoke-RestMethod @req4. Using Certificate
To use the certificate-based authentication method, you’ll need a valid X.509 certificate pair, which must be uploaded to the app registration. You can either create a self-signed certificate or use one issued by your internal certificate authority.
I’ve already covered the steps to create and upload the certificate in my other blog post: Connect to Microsoft Graph PowerShell Using Certificate. Follow those steps to generate and upload the certificate, then use below script to get the access token with Get-MsalToken and connect using either Connect-MgGraph or the REST API.
Using Certificate with Get-MsalToken
$TenantId = "<TENANT_ID>"
$ClientId = "<APP_CLIENT_ID>"
$Thumb = "<THUMBPRINT_NO_SPACES>"
$cert = Get-ChildItem "Cert:\CurrentUser\My\$Thumb"
if (-not $cert) { throw "Cert not found in CurrentUser\My: $Thumb" }
if (-not $cert.HasPrivateKey) { throw "Cert has no private key (need private key for app-only)." }
$token = Get-MsalToken -TenantId $TenantId -ClientId $ClientId -ClientCertificate $cert `
-Scopes "https://graph.microsoft.com/.default"After you get the access token, use below commands to connect to graph.
#Convert the access token to SecureString and connect
$secToken = ConvertTo-SecureString $token.AccessToken -AsPlainText -Force
#Connect to graph using access token
Connect-MgGraph -AccessToken $secTokenTroubleshooting
When connecting to Microsoft Graph using Get-MsalToken, you may encounter various error codes. Below, I’ll explain what these errors mean and how to resolve them.
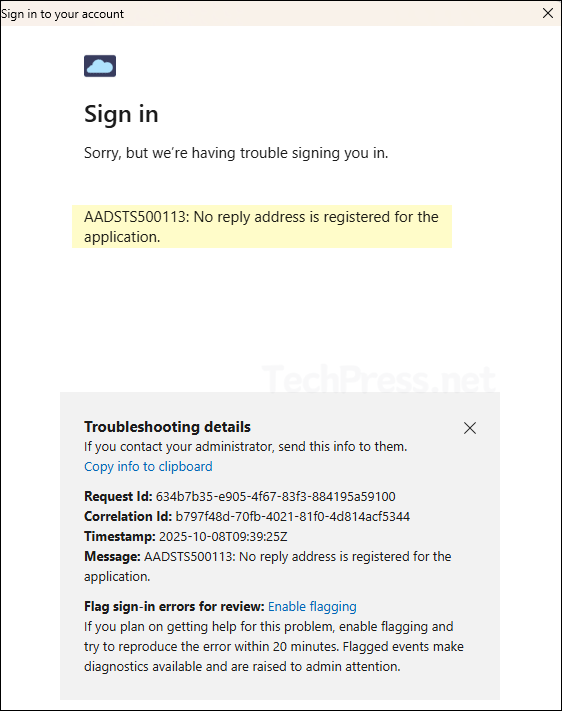
AADSTS500113
AADSTS500113: No reply address is registered for the application. This error means you’re doing an OAuth flow that returns to a redirect URI, but your app registration has no matching “Reply URL” (redirect URI) configured.
- You’re using authorization code / interactive auth (e.g., MSAL, Get-MsalToken -Interactive) and the app has no redirect URI.
- Or you pass a
redirect_urithat doesn’t exactly match what’s configured (scheme, host, path, port, trailing slash).
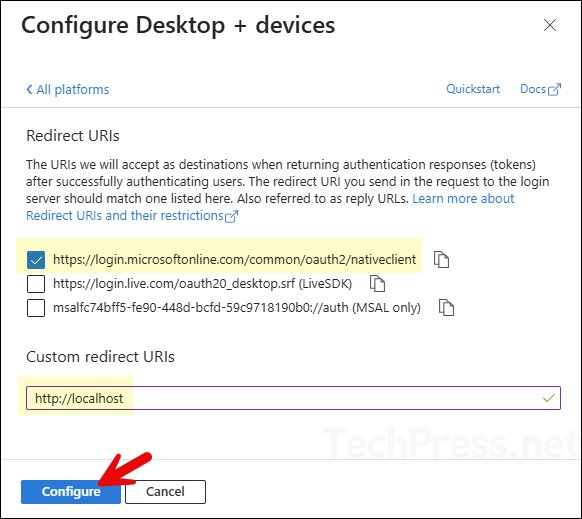
Follow below steps to fix this error code:
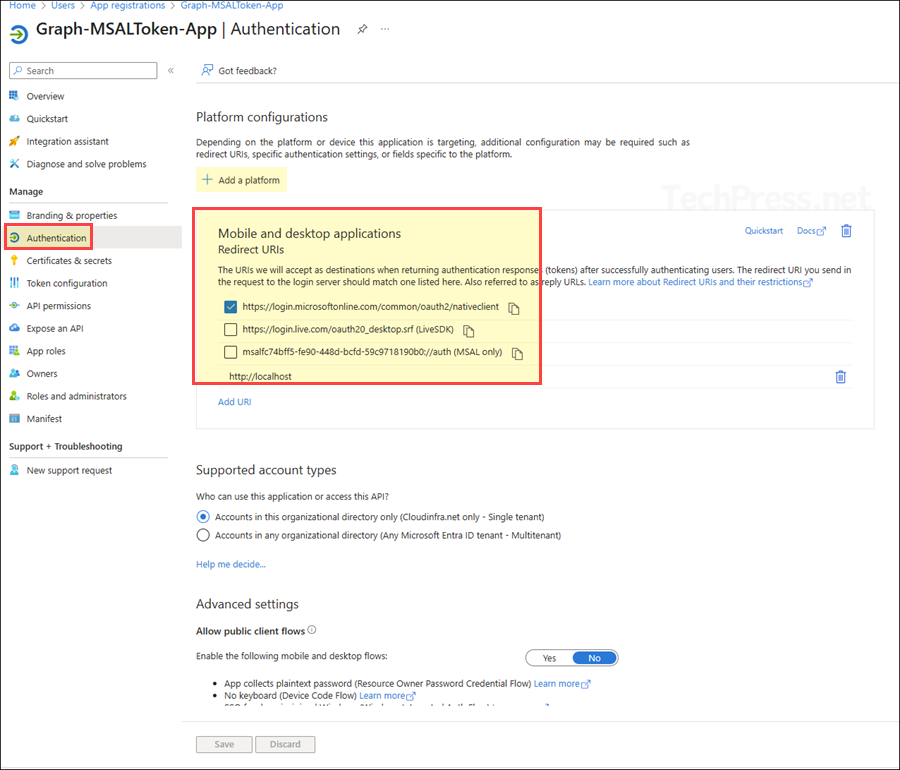
- Sign in to the Entra admin center > App registrations > Open the app > Authentication.
- Click on + Add platform and select Mobile and desktop applications.
- Add redirect URIs under Mobile and desktop:
- http://localhost
- https://login.microsoftonline.com/common/oauth2/nativeclient
- After adding the Redirect URIs, try to run the command again.
AADSTS7000218
This error code could be generated when you are trying to get the access token using a device code flow method. The command I have used was $token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -scopes $scopes -DeviceCode -RedirectUri “https://localhost” which resulted in the error code. Notice that I am using redirectUri switch which is not required.
AADSTS7000218
S C:\users\jatin> $token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -scopes $scopes -DeviceCode -RedirectUri "https://localhost"
To sign in, use a web browser to open the page https://microsoft.com/devicelogin and enter the code DMWKS7948 to authenticate.
Get-MsalToken : A configuration issue is preventing authentication - check the
error message from the server for details. You can modify the configuration in
the application registration portal. See https://aka.ms/msal-net-invalid-client
for details. Original exception: AADSTS7000218: The request body must contain
the following parameter: 'client_assertion' or 'client_secret'. Trace ID:
1dbc6271-794f-4def-961c-4a56d84f1000 Correlation ID:
e6c2fd0d-d820-4a4f-970d-e71df9bde357 Timestamp: 2025-10-08 12:21:48Z
At line:1 char:10
+ $token = Get-MsalToken -TenantId $tenantId -ClientId $clientId -scope ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : AuthenticationError: (Microsoft.Ident...arameterBui
lder:AcquireTokenWit...arameterBuilder) [Write-Error], MsalServiceException
+ FullyQualifiedErrorId : GetMsalTokenFailureAuthenticationError,Get-MsalToke
nTo fix this issue, I have Set Allow public client flows to Yes and click on Save and remove the switch -RedirectUri “https://localhost” from the command. This has fixed the issue for me.
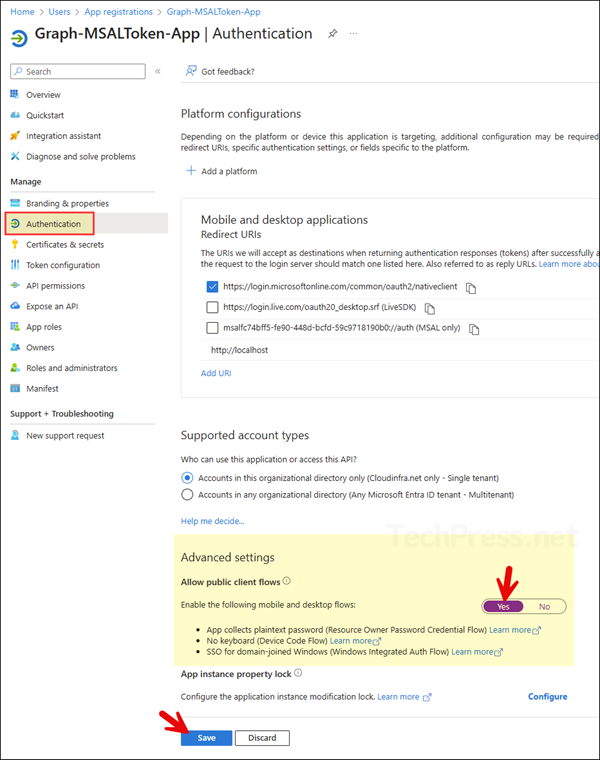
AADSTS7000215
This is another error I encountered while trying to fetch the access token using the Get-MsalToken command. The error occurred when using the client secret method to obtain the token. To fix this issue, verify the client secret value to ensure there are no typing errors. In my case, I hadn’t provided the client secret value and executed the Get-MsalToken command, which caused the error.
AADSTS7000215
Get-MsalToken : A configuration issue is preventing authentication - check the error message from the server for details. You can modify the configuration in the application registration portal. See
https://aka.ms/msal-net-invalid-client for details. Original exception: AADSTS7000215: Invalid client secret provided. Ensure the secret being sent in the request is the client secret value, not the client secret ID,
for a secret added to app 'fc94bff5-fe90-448d-bcfd-50c9718190b0'. Trace ID: 9fc5ae9b-758c-4d09-818a-1983244c9800 Correlation ID: d300f96c-3f36-4a4b-877c-f7e602918ab3 Timestamp: 2025-10-08 13:31:44Z
At line:14 char:10
+ $token = Get-MsalToken @msalParams
+ ~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : AuthenticationError: (Microsoft.Ident...arameterBuilder:AcquireTokenForClientParameterBuilder) [Write-Error], MsalServiceException
+ FullyQualifiedErrorId : GetMsalTokenFailureAuthenticationError,Get-MsalTokenConclusion
This blog post explained different ways to obtain an access token using the Get-MsalToken cmdlet and use it with either Connect-MgGraph or the Microsoft Graph REST API. If this method of connecting to Graph isn’t suitable for your scenario, there are alternative methods available. All of these are discussed in detail in my other blog post: How To Use Connect-MgGraph PowerShell Cmdlet.
