In this blog post, I will show you how to setup and configure LAPS for macOS via Intune. Microsoft Intune now supports Local administrator password solution (LAPS) for macOS devices. This feature allows you to create a local admin account and a standard local user account with a strong, random password (15 alphanumeric characters) during Automated Device Enrollment (ADE) profile deployment. These accounts once created would be fully managed by Intune. macOS LAPS feature was introduced in Intune service release 2507 (July 2025).
Similar to the Intune implementation of LAPS solution for Windows devices, local administrator account password is stored with the Entra ID device object. Password can be retrieved by the administrator with the required RBAC roles (discussed later). Intune will automatically rotate managed accounts password every six months.
Unique local account passwords are created using 15 characters with a mixture of lowercase and uppercase letters, numbers, and special symbols.
This guide will walk you through the prerequisites and configuration steps required to setup LAPS for macOS devices via Intune.
Contents
Prerequisites
- Intune service release 2507 (July 2025).
- Intune license assigned to the user.
- macOS 12 or later.
- Devices in Intune must sync from Apple business manager or Apple School manager.
- macOS device enrollment via Automated Device Enrollment (ADE) profile.
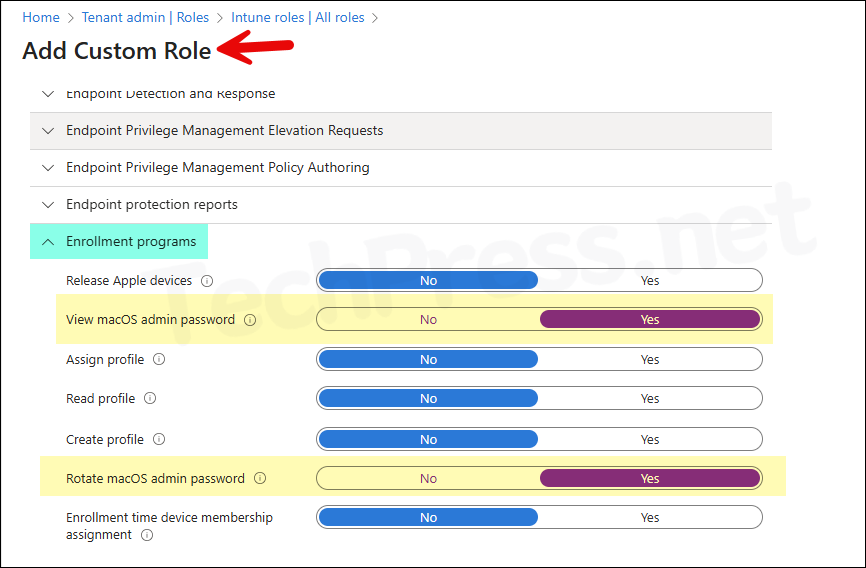
- RBAC permissions to view and rotate managed local administrator account password on macOS. These permissions are not included in any built-in admin roles, create a custom role in Intune and add below permissions:
- Category: Enrollment programs:
- Set Rotate macOS admin password to Yes
- Set View macOS admin password to Yes
- Category: Enrollment programs:
Important Points
- Intune automatically rotates the managed administrator or user account password every 6 months, however you can also manually rotate the password anytime from Intune admin center using remote device actions.
- If you want to create and manage local admin or local user accounts on Mac via Intune, the device must be provisioned with LAPS enabled ADE profile. LAPS config is applied only during ADE, therefore if a device is already enrolled into Intune, you will have to reenroll it.
- Ensure that the device is enrolled using ADE profile with User Affinity.
Steps to Configure LAPS for macOS
An Automated Device Enrollment (ADE) profile is required to setup and configure LAPS on macOS devices. Follow below steps to create a new ADE profile:
- Sign in to the Intune admin center > Devices > macOS > Enrollment > Enrollment Program Tokens > Select your token > Click on Create profile > macOS.
- Basics tab: Provide the name and description of the LAPS profile.
- Management Settings:
- User affinity: Enroll with User affinity
- Authentication method: Setup Assistant with modern authentication
- Await final configuration: Yes
- Locked enrollment: Yes
- Setup Assistant:
- Department: It will appear when users tap About Configuration during activation. For example, I will provide Business-Tech.
- Department Phone: Appears when users tap Need Help button during activation. For example, I will provide 123456798.
- Setup Assistant screens: Hide/show Setup Assistant screens during setup. Select the one’s as per your requirement and click Next.
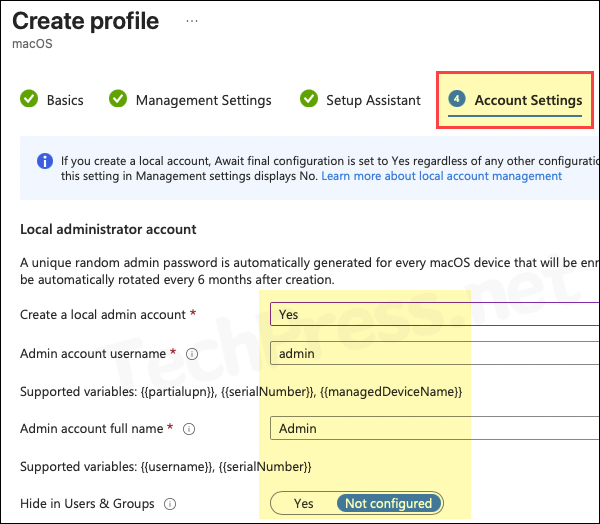
Account Settings tab
This is the tab for macOS LAPS configuration. Create and configure local admin and local user accounts from here.
Local Admin Account
- Create a local admin account: Yes
- Admin account username: Default value is Admin, you can customize it according to below supported values. As an example, you can use admin-{{serialNumber}} or just keep admin.
- {{serialNumber}}: for example, N49N00LNEEW1
- {{partialupn}}: for example, Jatin If an email address is [email protected].
- {{managedDeviceName}}: for example, N49N00LNEEW1_10_3/08/2025_09:45PM
- {{onPremisesSamAccountName}}: for example, techpress\Jatin
- Admin account full name: Provide a descriptive full name of the account. You can also use a variable {{username}} which will automatically convert it to user’s UPN value.
- Hide in Users & Groups: Keep it Not configured. If you select yes, admin account will be hidden from the sign-in window and in Users & groups.
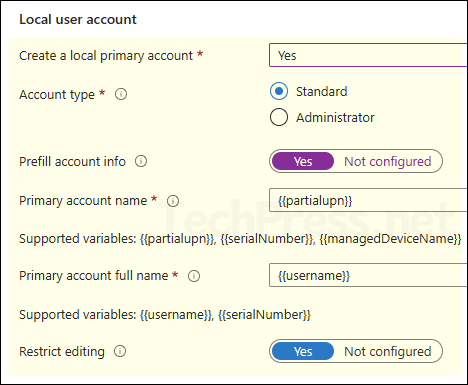
Local User Account
- Create a local primary account: Yes
- Account type: Standard
- Prefill account info: Yes (Intune will prefill username and full name during enrollment).
- Primary account name: {{partialupn}} (This is the part of user’s email before @, For example: [email protected] partialupn is jatin)
- Primary account full name: By default, intune will use {{username}}. Keep it default.
- Restrict editing: If you select this to Yes, user will not be allowed to change the prefilled account name or full name during setup.
- Review + create: Click Create.
Assignment of ADE Profile
- Open the ADE profile and click on Assign devices.
- Click on Add Devices, select your Intune enrolled macOS device to add.
End User Experience
After you enroll the Mac device using ADE profile, a local administrator and a standard user account (as configured in the profile) will be created. To check and confirm, follow the below steps:
- Sign in to your Mac device.
- Go to System settings > Users & Groups > Check if both the accounts are listed here.
Retrieve Local Admin Password
The local administrator account created using macOS LAPS will be full managed by Intune. Its password will be stored with the device object in Entra ID and can be retrieved either from Intune admin center or Entra admin center.
- Sign in to the Intune admin center > Devices > macOS > macOS devices.
- Click on the device that is targeted by the macOS LAPS policy.
- On left-hand side under Monitor category, find and click on Password and keys to check the local administrator account password and its last rotated date and time.
Rotate Local Admin Password
Local administrator password is rotated automatically every 6 months by Microsoft. You can also rotate the password manually from Intune admin center:
- Sign in to the Intune admin center > Devices > macOS > macOS devices.
- Click on the device that is targeted by the macOS LAPS policy.
- On left-hand side under Monitor category, find and click on Password and keys. To change the local admin password immediately, click Rotate local admin password option from the top menu. The password will be synced to the device during next Intune sync.
Troubleshooting
The configuration and deployment of LAPS for macOS is straightforward; however, you may encounter issues during profile deployment or when rotating the password. For example, if you recently changed the password and the new one is not yet showing in the Intune admin center. The password has been synced, but the administrator is unable to view it on Intune admin center, etc.
- Check the logs locally on macOS device or collect it remotely from Intune admin center. Logs provide useful information which can help troubleshoot LAPS related issues.
- If you have just rotated the local administrator account password, you will need to wait for Intune sync with the device to retrieve and store the new password in the database.
- If the password is synced and the administrator is unable to view the password, they need to ensure that the RBAC roles are assigned to their account for viewing and retrieving the password. Built-in roles do not include the permissions to view and rotate macOS device LAPS password, Create a custom role.
Custom RBAC role for macOS LAPS
You can create a custom role in Intune and set Rotate macOS admin password and View macOS admin password to Yes. Once these permissions are configured, assign the role to the administrators who will perform the following two actions:
- Rotate macOS admin password
- View macOS admin password
Audit Password Rotation
You can audit password rotations directly from the Intune admin center. This provides information about which admin account have viewed the local administrator passwords and which ones have rotated them. To check the audit logs, follow the below steps:
- Sign in to the Intune admin center, go to Tenant administration > Audit logs.
- Check the Get AdminAccountDto entry to find out who has viewed the admin password, and the rotateLocalAdminPassword ManagedDevice entry to determine when an admin password was last rotated.
