In this blog post, I’ll walk you through configuring Firefox SSO with Entra ID using Intune. Single sign-on in the Firefox browser is used to streamline authentication and enable seamless access to enterprise applications without repeated logins. Integrating Firefox with Entra ID enhances security, improves user experience, and ensures compliance across managed devices.
After you enable single sign-on (SSO) for Firefox on Windows devices, you no longer have to enter a username and password when a website requires authentication with Entra ID. It will automatically sign you in, which will significantly improve the user experience.
Starting with Firefox version 91, you can configure automatic user sign-in for accounts backed by a Microsoft cloud identity provider such as Entra ID. When you enable Windows SSO in Firefox using Intune, Firefox will use credentials stored on Windows to sign in to Microsoft work, and school accounts.
Before you can enable this configuration in the Firefox browser, you will need to download and import the necessary ADMX template for firefox into Intune.
Chrome SSO with Entra ID using Intune.
Related Blog Post
Contents
Download and Import Firefox ADMX templates
You can download Mozilla firefox ADMX templates from Github link: https://github.com/mozilla/policy-templates/releases. Download policy_templates_v6.7.zip and extract its contents. Go to the folder …\policy_templates_v6.7\windows where you will find mozilla.admx and firefox.admx file. You will also need its corresponding mozilla.adml and firefox.adml file which can be located at …\policy_templates_v6.7\windows\en-US.
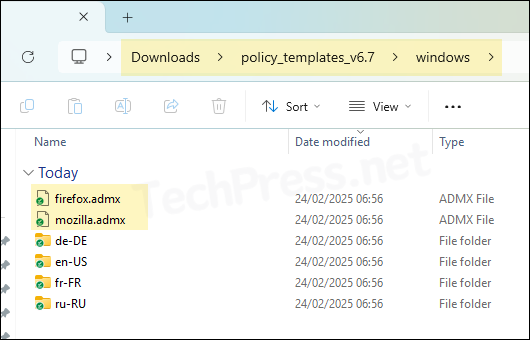
Upload template files in Intune by going to Intune Admin Center > Devices > Configuration > Click on Import ADMX > Click on +Import. You will first have to upload mozilla.admx and thereafter firefox.admx template. If you try to upload firefox.admx template first, you will get the error: ADMX file referenced not found NamespaceMissing:Mozilla.Policies. Please upload it first.
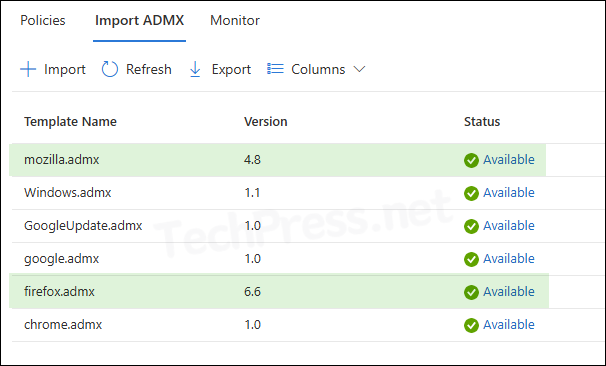
Both mozilla.admx and firefox.admx template files are uploaded in Intune.
Enable Firefox SSO with Entra ID Intune Policy
Once you have imported all the required ADMX template files in Intune, you can create a device configuration policy as shown below:
- Sign in to Intune admin center > Devices > Windows > Configuration > Create > New Policy.
- Platform: Windows 10 and later
- Profile type: Templates.
- Template Name: Imported Administrative templates
- Click Create.
- On the Basics tab, provide a Name and Description of the policy and click Next.
- On Configuration settings tab, navigate to Mozilla\Firefox and search using keyword Windows SSO. Click on the setting and set it to Enabled.
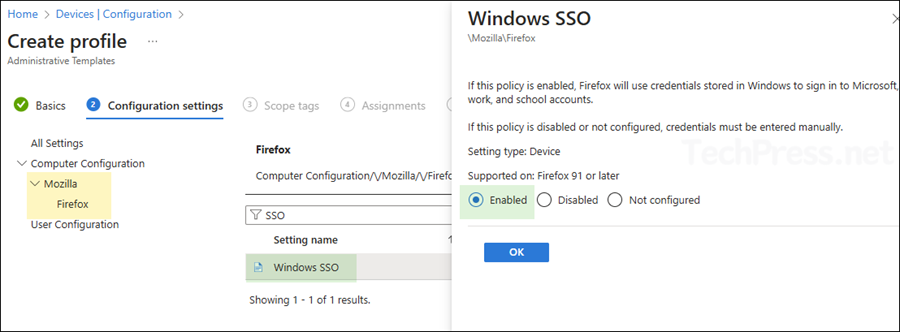
- Scope tags: Click Next
- Assignments: Assign this policy to an entra security group containing users or devices. It’s a best practice to test the policy on a few devices first. If it’s working fine, then extend it to other devices.
- Review + create: Review the policy settings and click on Create.
Monitoring Firefox SSO Intune Policy
- Sign in to the Intune admin center > Devices > Configuration.
- Select the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
After the deployment is successfully completed, launch a website in the Firefox browser that requires authentication with Entra ID. You will be automatically signed in without the need to enter a username and password. The credentials you used to sign in to the Windows device will be passed through for automatic sign-in to the web app, which requires Microsoft cloud authentication.
To confirm if the configuration has been applied to the firefox browser. Launch Firefox browser and go to the Settings.
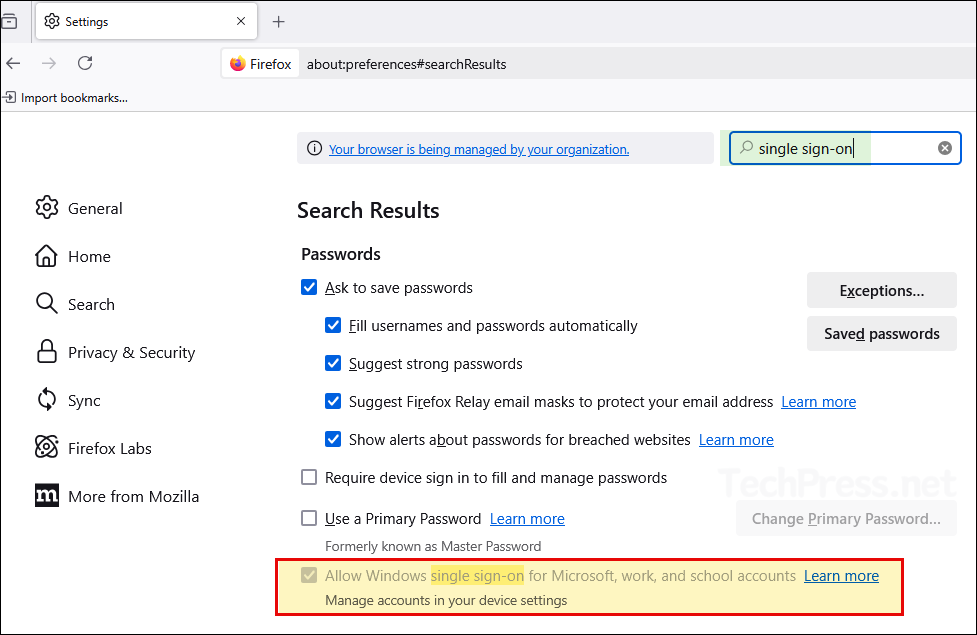
Search for single sign-on and you will find a setting Allow Windows single sign-on for Microsoft, work, and school accounts checked and greyed out. This means that this setting is enabled and being managed by intune.
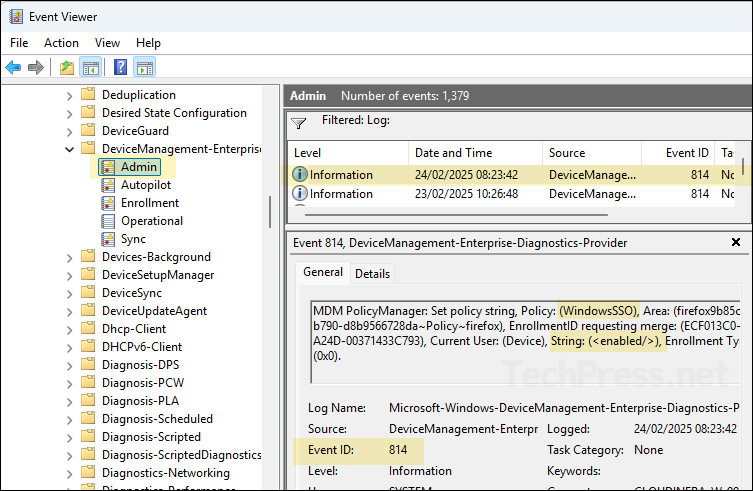
To find logs related to your SSO configuration deployment, open Event viewer> application and services logs> Microsoft > Windows > device management-enterprise-diagnostics-provider> Admin. Right-click on Admin folder > Filter Current log. Filter it using Event ID 814.